The Last Algorithm
2026 might be the year continuous algorithm approaches start to generalize into universal problem solvers
This is some of my favorite, most popular, and latest content. You can also browse and search the archives.
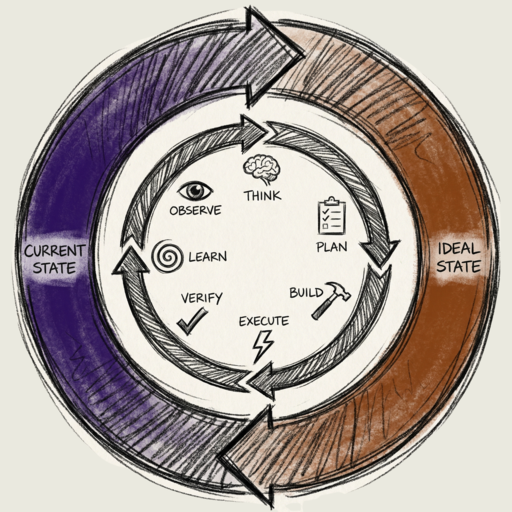
2026 might be the year continuous algorithm approaches start to generalize into universal problem solvers
Even if Claude Code were the actual addiction, it would still be better than porn, TikTok, and Netflix

Looking back at my predictions to see what I got right, wrong, and what's still playing out
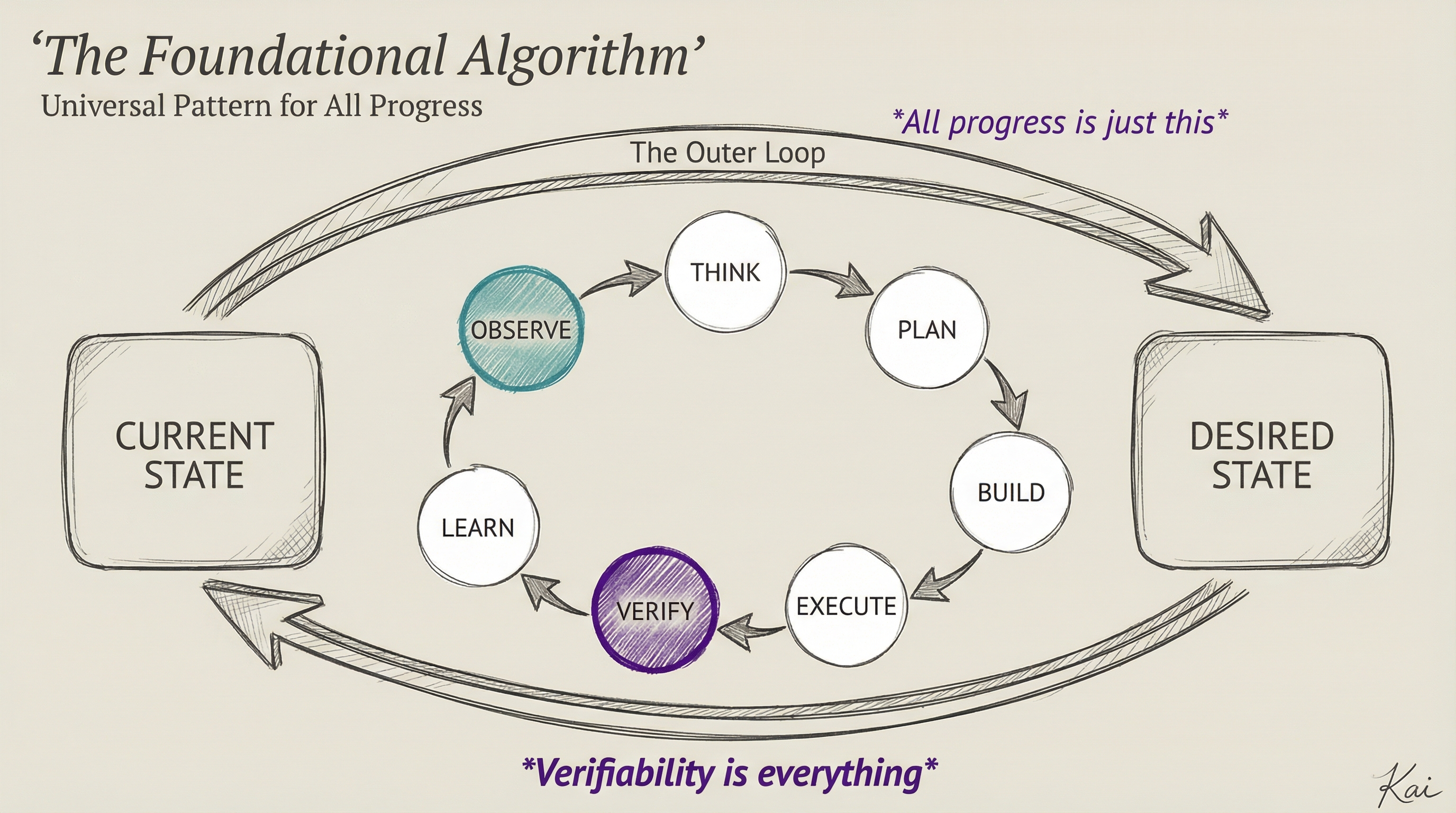
My thoughts on what's coming for AI in 2026

My thoughts on what's coming for Cybersecurity in 2026

People are building their own software instead of paying for imperfect apps

We're not so much competing with China as we are with our own failures

9 tiers of personal AI progress, from chatbots to a full AI companion