Web Application Security Testing Resources

Web Application Security Testing Methodologies >
Security assessments in general, and certainly web security assessments, are nearly as much art as science, so everyone has their own favorite method. Below are a few of the main methodologies that are out there.
Web Application Hacker’s Handbook Checklist ( >http://portswigger.net/wahh/tasks.html >)
[ **Reproduced with permission from authors; copyright Dafydd Stuttard and Marcus Pinto ]
Recon and Analysis
Test Handling of Access
Test the Handling of Input
Test Application Logic
Assess Application Hosting
Miscellaneous Tests
Web Application Hacker’s Handbook Testing Methodology [From >Chapter 20 > of the WAHH]
[ **Reproduced with permission from authors; copyright Dafydd Stuttard and Marcus Pinto ]
Notice that this methodology is quite different from the checklist provided above. Also keep in mind that the book itself provides additional detailed steps in each of the sections listed. This is meant to help one compare methodology approaches, not to provide the actual content.
Map the Application’s Content
Analyze the Application
Test Client-side Controls
Test the Authentication Mechanism
Test the Session Management Mechanism
Test Access Controls
Test for Input-Based Vulnerabilities
Test for Function-Specific Input Vulnerabilities
Test for Logic Flaws
Test for Shared Hosting Vulnerabilities
Test for Web Server Vulnerabilities
Miscellaneous Checks
The OWASP Testing Methodology Checklist ( >https://www.owasp.org/index.php/Testing_Checklist >)
Information Gathering
Configuration Management Testing
Authentication Testing
Session Management
Authorization Testing
Business Logic Testing
Data Validation Testing
Denial of Service Testing
Web Services Testing
Web Services Testing
Web Services Testing
<
h2>OWASP ASVS >
The OWASP ASVS is a phenomenal testing methodology for faster tests where your primary goal is making sure you’re not missing something major.
It breaks things down by the risk of the application you’re testing, based on three levels:
Level 1: Opportunistic, meant for all software
Level 2: Standard, for applications that contain sensitive data that requires protection
Level 3: Advanced, for the most critical applications
The testing sections cover the following.

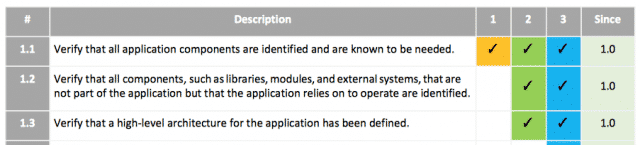
And for each of those sections you get a table that looks like this:
Suites / Frameworks >
Burp Suite >The premier tool for performing manual web application vulnerability assessments and penetration tests. The pro version includes a scanner, and the Intruder tool makes the offering stand out amongst its peers.
NetsparkerOne of the best automated scanning tools on the market right now, which is why I’m currently doing a sponsorship deal with them for the site. For automated scanning I’d say that Netsparker and WebInspect are pretty close in quality of results, with every other tool being significantly behind.
HP WebInspectAn enterprise-focused tool suite that includes a scanner, proxy, and assorted other tools.
WebScarabNGThe latest version of this famous suite from OWASP. Includes a web services module that allows you to parse WSDLs and interact with their associated functions.
IBM AppScan >IBM’s enterprise-focused suite.
Arachni >
Acunetix >Acunetix’s enterprise-focused suite.
AppSpider >Rapid 7’s enterprise-focused suite, based on the NTObjectives scanner.
W3af >W3af is a Web Application Attack and Audit Framework. The project’s goal is to create a framework to find and exploit web application vulnerabilities that is easy to use and extend.
Websecurify >Websecurify is a powerful web application security testing environment designed from the ground up to provide the best combination of automatic and manual vulnerability testing technologies.
Samurai >Samurai is another web scanner by InGuardians.
Skipfish >A fully automated, active web application security reconnaissance tool written by Michal Zalewski of Google.
RAFT (Response Analysis and Further Testing Tool) >RAFT is a testing tool for the identification of vulnerabilities in web applications. RAFT is a suite of tools that utilize common shared elements to make testing and analysis easier. The tool provides visibility in to areas that other tools do not such as various client side storage.
Zed Attack Proxy (ZAP) >The Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications. It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing. ZAP provides automated scanners as well as a set of tools that allow you to find security vulnerabilities manually.
Standalone Web Assessment Tools >
NiktoNikto is an command line Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1000 servers, and version specific problems on over 270 servers.
WiktoWikto is Nikto for Windows – but with a couple of fancy extra features including Fuzzy logic error code checking, a back-end miner, Google assisted directory mining and real time HTTP request/response monitoring. Wikto is coded in C# and requires the .NET framework.
Web Assessment Utilities >
Yehg.net Charset Encoder / String Encrypter >A online, feature-rich tool for changing the encoding of input.
Browser Extensions >
Websecurify Chrome Extension >The Chrome Extension version of the Websecurify tool. Performs a scan and tells you the results summary, but there’s no authentication or detailed view of findings. It’s more of a quick-touch option before you run a real tool.
XSS MeThe Firefox Extension.
SQL Inject MeThe Firefox Extension.
Vulnerable Test Websites >
These sites are purposely vulnerable for the purpose of testing web app security scanners. They are designed for this purpose, but I’d check to make sure it’s ok before scanning them (just to be sure).
Internet-accessible
Google Gruyere >This one is from Google and you can do it both online and as a local install.
zero.webappsecurity.com (HP) >I happen to know this one is o.k. to scan.
test.acunetix.com (Acunetix)
testphp.vulnweb.com (Acunetix)
testasp.acunetix.com (Acunetix)
testaspnet.acunetix.com (Acunetix)
Hacker Test >This one is not like the others; it’s not a full website you’d scan, but rather more like a puzzle where you proceed through various levels.
Hax.tor >Another challenge, similar to Hacker Test.
The Enigma Group >A beginner-focused online resource for web hacking.
HACKME GameA software security learning game.
OWASP HackademicAn OWASP project aimed at helping people learn web security through a series of challenges.
Test Page for the x5s ToolA test page for XSS meant to be used with the X5S tool.
Download and Configure
Broken Web Apps Project (OWASP) >This is the one you want first; it has over a dozen broken web apps to play with.
Bonsai MothA VMware image with a collection of broken web applications that you can use for testing web scanners and static analysis tools as well as providing an intro to webappsec.
Web Security Dojo (Maven)Similar to OWASP’s Broken Web Apps project, i.e. multiple broken web apps in one place.
Webgoat (OWASP) >This is the grand pubah of the testing sites because it includes training with it. Note that it’s on the Broken Web Apps image listed above.
BadStore
Hackme Bank (McAfee)
Hackme Casino (McAfee)
Moth (Bonsai)
Google Gruyere >This one is from Google and you can do it both online and as a local install.
Bodgeit >This is a project named Bodgeit hosted with Google.
Hackxor >
MultiDae >
Peruggia >
SQLol >
Web Security Dojo
Additional Resources >
Hellbound Hackers
p0wnlabs
Watcher Tests
References >
In adding to the lists of vulnerable sites over the years I’ve benefitted from other lists on the Internet, including Astyran which I believe to be a phenomenal websec resource in general.