More Captured Mirai Botnet Traffic Analysis
So, related to this post >, I did some more analysis by letting a listener run for almost a day.
Here’s what I got:
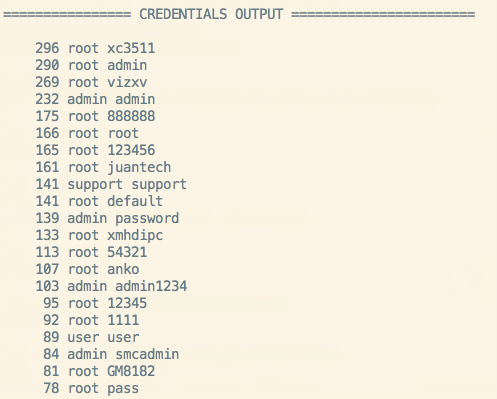
Credentials
These are the top n results. The first number is the number of times that combo was used.
296 root xc3511
290 root admin
269 root vizxv
232 admin admin
175 root 888888
166 root root
165 root 123456
161 root juantech
141 support support
141 root default
139 admin password
133 root xmhdipc
113 root 54321
107 root anko
103 admin admin1234
95 root 12345
92 root 1111
89 user user
84 admin smcadmin
81 root GM8182
78 root pass
71 root klv123
69 root 5up
67 root Zte521
67 guest 12345
65 root 1234
63 guest guest
58 admin 1111
Countries
160 UA (Ukraine)
150 VN (Vietnam)
118 CN (China)
81 TW (Taiwan)
76 BR (Brazil)
66 TR (Turkey)
50 IN (India)
46 RU (Russia)
39 US (United States)
30 PL (Poland)
22 FR (France)
21 MX (Mexico)
20 RO (Romania)
20 KR (South Korea)
16 TH (Thailand)
12 CR (Croatia)
11 SE (Sweden)
11 AR (Argentina)
10 ID (Indonesia)
10 GB (Great Britain)
10 CO (Columbia)
Summary
I’m not sure what we can infer from the top, say, five credentials are being used. Perhaps that there are more of them. Perhaps that there are more vulnerable versions of the devices that those creds are associated with. Maybe nothing. It’s something I’ll probably look at closer when I have time.
As for the countries, the top countries are interesting, the Ukraine and lots of Asia, then Brazil and Turkey. Russia and the United States ranked lower than I would have imagined.
Anyway, just wanted to post some stats. Will do more analysis later.