A Shodan Tutorial and Primer
What is Shodan? >
Shodan is a search engine for finding specific devices, and device types, that exist online. The most popular searches are for things like webcam, linksys, cisco, netgear, SCADA, etc.
It works by scanning the entire Internet and parsing the banners that are returned by various devices. Using that information, Shodan can tell you things like what web server (and version) is most popular, or how many anonymous FTP servers exist in a particular location, and what make and model the device may be.
Shodan is of particular use for security research around the Internet of Things, since there will soon be billions of devices online that 1) have specific vulnerabilities that need to be fixed, and 2) can be identified quickly by their banner information.
Basic Usage >
You start by navigating to the main page, and then entering into the search field, like you would any other search engine.
For this search, I looked for "VNC".
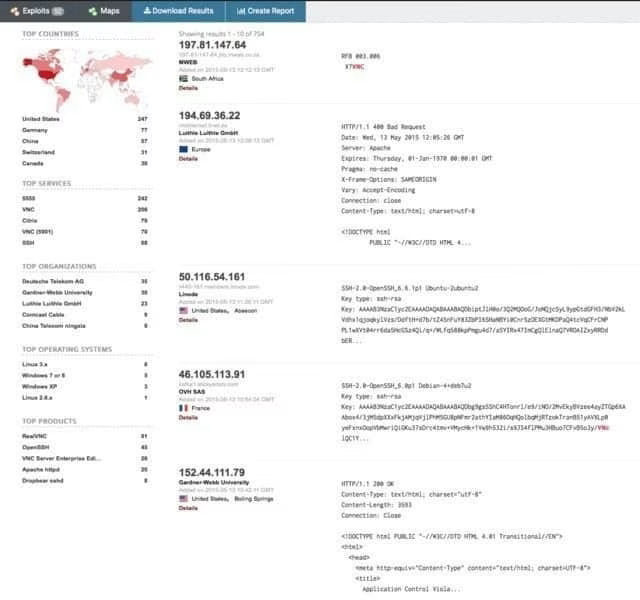
From there you can pivot to a few key areas in the results. Starting on the left sidebar, we see a good amount of summary data:
Results map
Top services (Ports)
Top organizations (ISPs)
Top operating systems
Top products (Software name)
Then in the main section we get the full results list, including:
IP address
Hostname
ISP
When the entry was added to the database
The country it’s located in
The banner itself
Then, for even more information you can click details, which takes you into that host itself:
When in details mode for a given host, the URL changes from the search structure to the following: https://www.shodan.io/host/194.69.36.22.
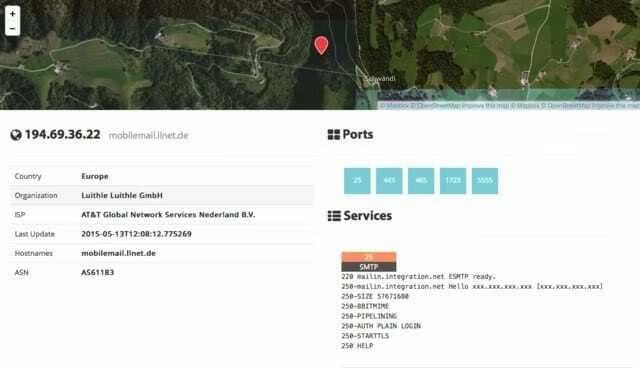
Here you see the data about the host on the left, the list of ports that were found at the top right, and then the individual port details and banners from each port as you go down the page. It’s a clean layout.
Using Filters >
As with any search engine, Shodan works well with basic, single-term searches, but the real power comes with customized queries.
Here are the basic search filters you can use:
city: find devices in a particular city
country: find devices in a particular country
geo: you can pass it coordinates
hostname: find values that match the hostname
net: search based on an IP or /x CIDR
os: search based on operating system
port: find particular ports that are open
before/after: find results within a timeframe
Search Examples >
You can drop the quotes sometimes, on some queries, but you often need them. I recommend you just use them all the time, because that always works.
Find Apache servers in San Francisco:
apache city:"San Francisco"
Find Nginx servers in Germany:
nginx country:"DE"
Find GWS (Google Web Server) servers:
"Server: gws" hostname:"google"
Find Cisco devices on a particular subnet:
cisco net:"216.219.143.0/24"
So you basically have some sort of base search term you’re looking for (shown in orange) and then you narrow down your search using the filters like we see above.
Use cases
You can use the "Explore" button on the main Shodan site to look at common searches and results, which are illuminating. You’ll find things like:
Webcams
SCADA
Traffic lights
Routers
Default passwords
Etc.
It’s interesting. It’s exciting. It’s frightening.
Combining filters
To combine filters, simply keep adding them on. You can also do this by clicking filters in the left sidebar for a given result set. So if you want to search for Nginx servers in San Francisco, that are running on port 8080, that are also running Tomcat, you could do the following:
Apache city:"San Francisco" port:"8080" product:"Apache Tomcat/Coyote JSP engine"
The full product name was added in this case by clicking on the product in the left sidebar. Disregard the line break in the query.
Advanced Usage >
Here are a few other cool things you can do with the service.
Data Export: You can export your results in various formats using the top menu after you’ve performed a search.
Browser Search: You can configure your browser to search Shodan when you search from the URL bar.
Shodan Free Account: You should create and log in to your free account when you search, as the interface is pretty nerfed if you don’t, e.g. not being able to see host information, etc.
Premium Accounts: A premium account is a one-time payment of $45 and it gives you increased access to the API. Full details and docs are available at https://developer.shodan.io >.
Summary
I really love this project, and I hope this short introduction will get you using it as well.
Notes
This resource is just an intro to what Shodan is and how to do the basics to what Shodan is and how to do the basics. You should also take a look at the help pages which are quite good.
The project currently tests for around 200+ services.
Shodan uses its own internally developed port scanner, not Nmap or Zmap.
The system works off of banners, and banners can be modified, spoofed, and faked. What you see is what’s being presented, not necessarily what is real.
You should also check out the blog at https://blog.shodan.io >.