A ffuf Primer
ffuf is an acronym for "fuzz faster you fool!", and it’s a cli-based web attack tool written in Go. Veteran web testers might think of it as Burp Intruder on the command line.
The hardest thing about ffuf is figuring out how to pronounce it. It’s just "fluff", without the "l".
Once you get the main concept, it’s brilliantly simple. Basically, you have two things:
The input file you’re sending to the web app, and
The location that’s being injected, indicated by the word FUZZ
From there, you just line up exactly what you want to attack using which list, which pairs really well with Seclists > for picking stuff to send.
Examples
The tool is extremely intuitive to use. Here we’re just supplying a wordlist with -w, adding colored output for interesting stuff with -c, and we’re sending our list against the root of the site where the FUZZ string is.
1. Find pages or files in the root of a site
ffuf -c -w /path/to/list -u https://tesla.com/FUZZ
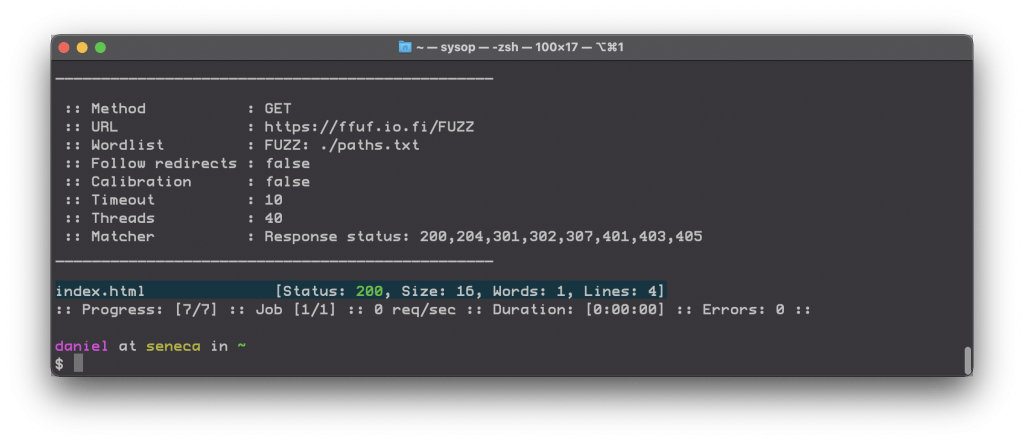
Output showing one 200 found
My favorite list for this is the curated.txt > list.
My project, RobotsDisallowed >, looks for the most commonly disallowed paths on the internet, so that seems like a good list to use with ffuf for every target.
2. Find commonly-disallowed paths on your target using RobotsDisallowed
The curated.txt list within RobotsDisallowed filters the top 10,000 most commonly disallowed paths for sensitive words, such as user, admin, password, login, etc., which means if you get a hit you have a higher chance of finding something interesting.
ffuf -c -w /path/to/curated.txt -u https://tesla.com/FUZZ
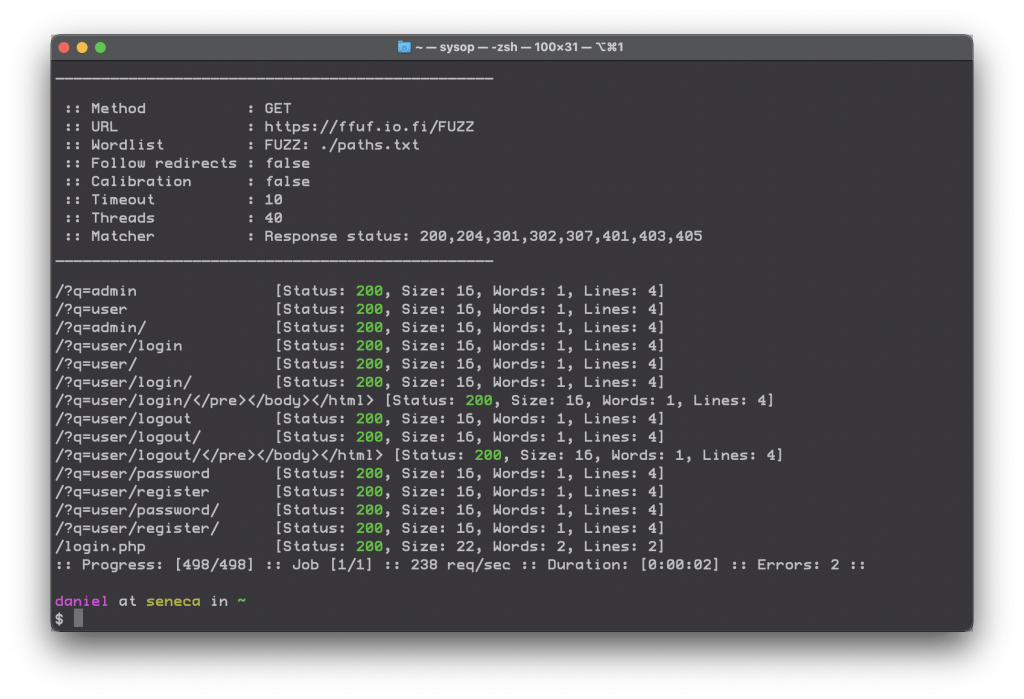
Ffuf and curated.txt against Tesla.com
3. Directory discovery a la dirbuster
Tools like this are so flexible that they can replace the need for others that only do one thing.
Using this same method, you can emulate the functionality of tools like Dirbuster.
ffuf -c -w /path/to/directories.txt -u https://tesla.com/FUZZ
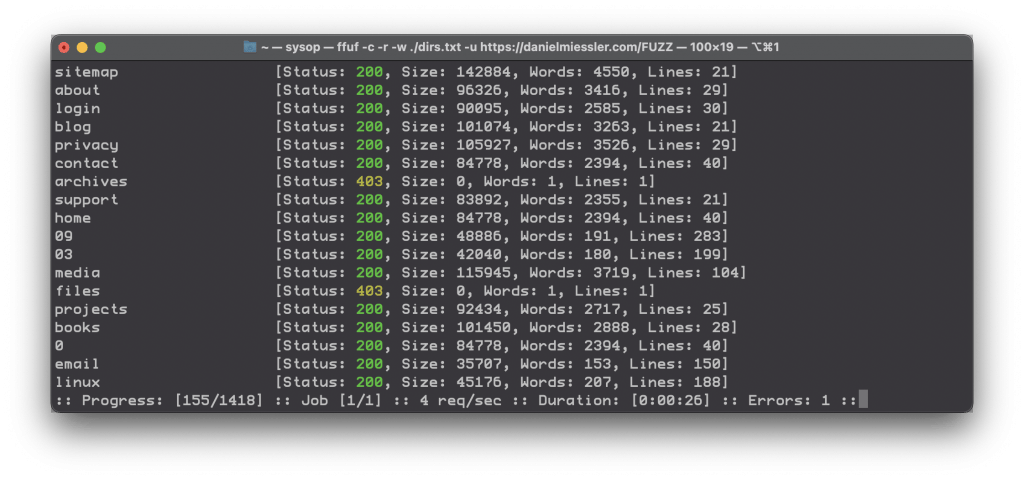
Finding directories with ffuf a la dirbuster
4. Attacking GET parameter names
Remember, you can throw stuff at any part of the site you define, and that includes GET parameters.
ffuf -c -w /path/to/parameters.txt -u https://target/script.php?FUZZ=test_value
Here we’re fuzzing the name of the parameter, for example to see if you can provide a parameter that you haven’t seen yet but will still work. But you can also attack the value of a parameter that you have the name of.
5. Attacking GET parameter values
If already have the name of a parameter you want to attack, just move the FUZZ value.
ffuf -c -w /path/to/parameters.txt -u https://target/script.php?valid_name=FUZZ
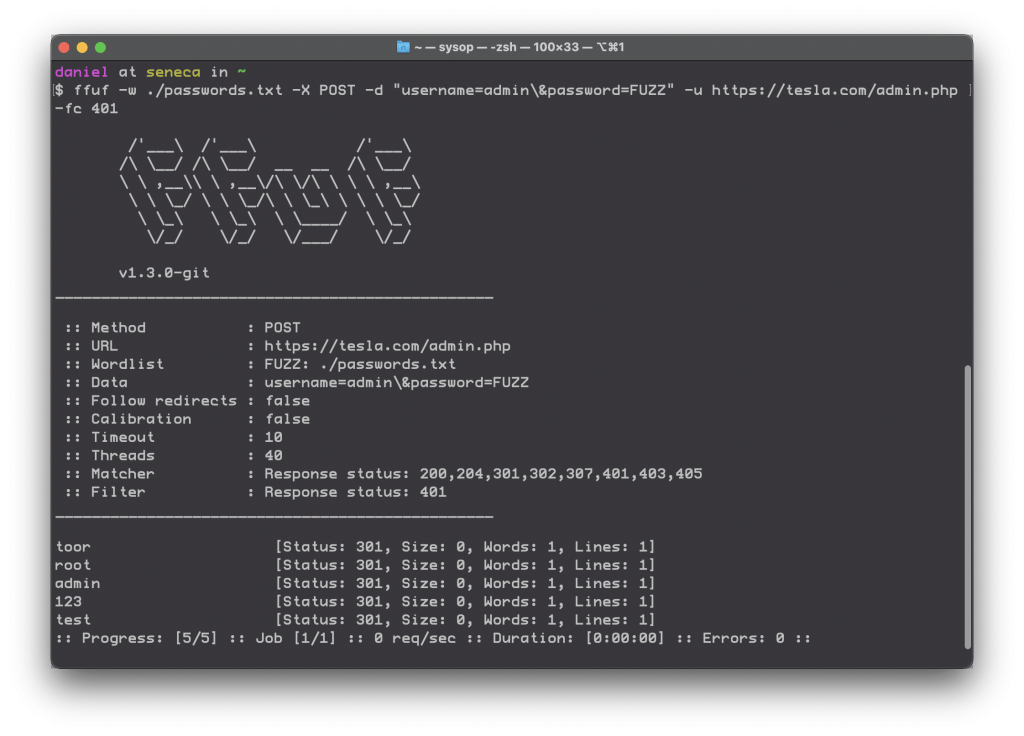
6. Guessing passwords by attacking POST data
How many tools have we emulated so far? Four?
Now we’re checking usernames and passwords, using the same tool. That’s flexibility!
ffuf -c -w /path/to/passwords.txt -X POST -d "username=admin\&password=FUZZ" -u https://target/login.php
7. Fuzz multiple locations and only match locations that match a particular keyword
Here’s a wicked one from the manual.
ffuf -w params.txt:PARAM -w values.txt:VAL -u https://example.org/?PARAM=VAL -mr "VAL" -c
Options
Ok, now that you have the feel for it, let’s look at some options you can add.
Basics
-u: the target URL
-c: add color to output
-r: follow redirects
-t: timeout in seconds (default 10)
-x: send through a proxy
Types of requests
-d: data you’re going to send over POST
-H: the header value(s) you’re sending (multiple allowed)
-b: send cookie values
Useful filters
You can use -fl instead of -ml to filter instead of directly match.
-mc: match for certain HTTP codes
-ml: match based on the number of lines in the response
-ms: match based on the size of the response
-mw: match based on the number of words in the response
Miscellaneous
-e: add additional FUZZ keywords
-request: a file containing a raw request
-o: write the output to a file
-mw: match based on the number of words in the response
Summary
ffuf is a highly flexible cli-based attack tool for web hacking
You can supply your own lists and attack various parts of the URL and site with extreme precision
It replaces multiple other tools, such as Dirbuster and Hydra-like password guessers
Like I said in the beginning, ffuf is basically a cli-based version of Intruder, and I highly recommend it as part of any web tester’s toolkit.