amass — Automated Attack Surface Mapping
Whether you’re attacking or defending, you have the highest chance of success when you fully understand the target.
Summary >
The pronunciation stress is on the second syllable.
amass > (/əˈmas/) is a versatile cybersecurity tool for gathering information on the attack surface of targets in multiple dimensions, and this amass tutorial will take you through its most important and powerful features, including many examples.
Why amass?
For example, there are many port scanners, but nmap and masscan provide 99% of the value.
You might be asking, "Why amass and not one of the 113 other tools out there?" It’s a good question, and part of the answer is because yes—there really is a legion of tools out there that all do one or two things decently—and it’s refreshing to have this level of quality across so many features all in one place.
I’ve just become a contributor to the project as well (June 2019).
amass also prioritizes the use of many different sources of input, whereas many tools only have a few. So when a new technique comes out—such as certificate transparency—the developers are quick to include it. Here’s a short list of all the different things it looks at:
DNS: Basic enumeration, Brute forcing (upon request), Reverse DNS sweeping, Subdomain name alterations/permutations, Zone transfers (upon request)
Scraping: Ask, Baidu, Bing, CommonCrawl, DNSDumpster, DNSTable, Dogpile, Exalead, FindSubdomains, Google, HackerOne, IPv4Info, Netcraft, PTRArchive, Riddler, SiteDossier, ViewDNS, Yahoo
Certificates: Active pulls (upon request), Censys, CertDB, CertSpotter, Crtsh, Entrust
APIs: AlienVault, BinaryEdge, BufferOver, CIRCL, DNSDB, HackerTarget, Mnemonic, NetworksDB, PassiveTotal, RADb, Robtex, SecurityTrails, ShadowServer, Shodan, Sublist3rAPI, TeamCymru, ThreatCrowd, Twitter, Umbrella, URLScan, VirusTotal
Web Archives: ArchiveIt, ArchiveToday, Arquivo, LoCArchive, OpenUKArchive, UKGovArchive, Wayback
@caffix >, @fork_while_fork >, and the rest of the team are phenomenal.
Finally, tools develop their own gravity once they get big enough, popular enough, and good enough. In the OSINT/Recon tools game, there exists a depressing graveyard of one-off and abandoned utilities, and it’s nice to see a project with some consistent developer attention.
Installation
Here are the best ways to install amass.
You’ll need to make sure your Go pathing is set up correctly so you can run it. You might need a chicken to kill.
Go
go get -u http://github.com/OWASP/Amass/…amass enum –list
Docker
docker build -t amass https://github.com/OWASP/Amass.gitdocker run -v ~/amass:/amass/ amass enum –list
Homebrew/macOS
brew tap caffix/amassbrew install amassamass enum –list
Snap
sudo snap install amassamass enum –list
The Modules
amass is somewhat unique in that all its functionality is broken into modules that it calls subcommands, which are intel, enum, viz, track, and db.
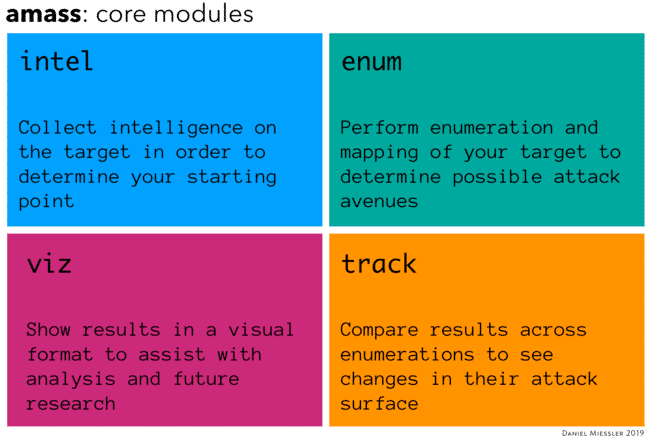
The primary amass modules
There’s a full user guide > that functions much like a man page, and you can use that as a full reference. But here we’ll cover the basic themes and show a few of my favorite options.
In short, intel is for finding information on the target, enum is for mapping the attack surface, viz is for showing results, and track is for showing results over time. db is for manipulating the database of results in various ways.
Intelligence
Consult the full user guide > for more detail on each.
If you’re not doing adequate recon, you’re setting yourself up to be unpleasantly surprised in the future.
If you have a new target and are only using amass, the Intelligence subcommand is where you’ll start. It takes what you have and helps you expand your scope to additional root domains. Here are some of my favorite options under the intel subcommand.
intel: -addr (by IP range), -asn (by ASN), -cidr (show you domains on that range), -org (to find organizations with that text in them), and -whois (for reverse whois).
I’m using Uber because they are known to have an open bounty program that encourages this sort of public scrutiny.
Let’s look at organizations with "uber" in their name.
amass intel -org uber
A few of those should stand out (and not just because I highlighted them).
Results abridged for brevity.
18692, NEUBERGER - Neuberger Berman 19796, SHUBERT - Shubert Organization 42836, SCHUBERGPHILIS 45230, UBERGROUP-AS-NZ UberGroup Limited 52336, Autoridad Nacional para la Innovaci�n Gubernamental 54320, FLYP - Uberflip 56036, UBERGROUP-NIX-NZ UberGroup Limited 57098, IMEDIA-AS Pierre de Coubertin 3-5 office building 63086, UBER-PROD - Uber Technologies 63943, UBER-AS-AP UBER SINGAPORE TECHNOLOGY PTE. LTD 63948, UBER-AS-AP UBER SINGAPORE TECHNOLOGY PTE. LTD 132313, UB3RHOST-AS-AP Uber Technologies Limited 134135, UBER-AS-AP Uber Technologies 134981, UBERINC-AS-CN Uber Inc 135072, SUITCL-AS-AP Shanghai Uber Information Technology Co. 135190, UBERCORE-AS Ubercore Data Labs Private Limited 136114, IDNIC-UBER-AS-ID PT. Uber Indonesia Technology 267015, ESADINET - EMPRESA DE SERVICOS ADM. DE ITUBERA LTD
And here’s a lookup based on a CIDR range, where you can find all the domains hosted on that range.
amass intel -ip -src -cidr 104.154.0.0/15
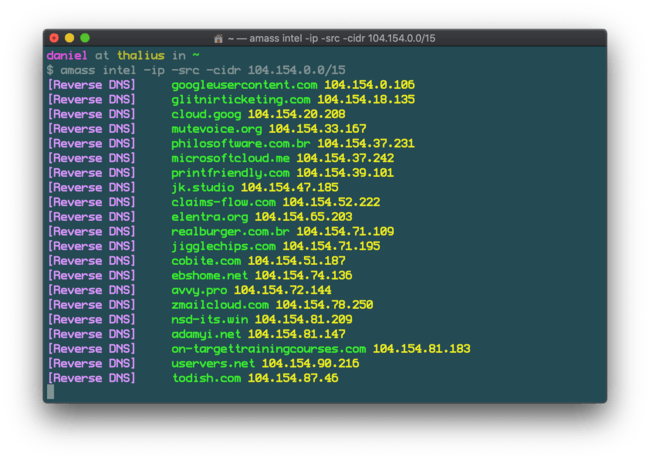
Finding domains hosted on a CIDR range
Enumeration
Automated recon workflows are one of the most useful capabilities for any OFFSEC practitioner.
The most basic example is just finding subdomains for a given domain. Here we use the -ip option to show the IPs for them as well.
amass enum -ip -d danielmiessler.com
I also love that amass output almost looks like a GUI, but can still be parsed via CLI.
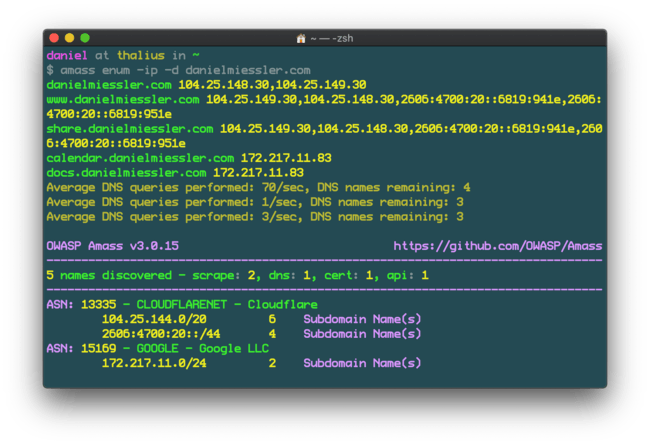
With the IP option showing IPS for discovered domains
And here’s a run using the very cool -demo option, which does some quasi-masking of the output.
You might think I shouldn’t show my DNS like this, but I run WordPress so you can hack me with a wet piece of string anyway.
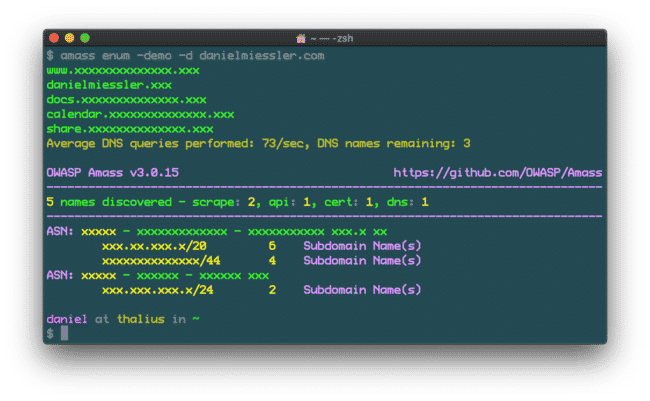
The enum module used with the demo option
Some of my favorite options in enum are:
- enum: -d for basic subdomains, -brute brute-forcing additional subdomains, and -src because it lets you see what techniques were used to get the results.
Visualization
amass viz -d3 domains.txt -o 443 /your/dir/
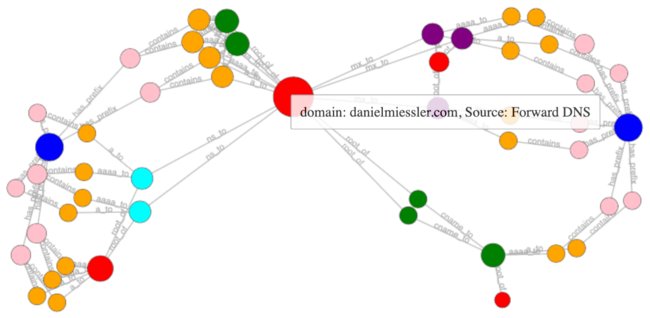
d3 output from amass against danielmiessler.com
My favorite options in viz are: -d3 for the D3 output, -maltego for creating Maltego compatible output, and -visjs for an alternative JS visualization that’s kind of nice.

amass in action
Real-world Examples
The difference between decent and extraordinary OFFSEC people often comes down to their skills in recon and OSINT.
Ok, so that was a brief intro into the tool, and again—the user guide > has tons more options for things you might expect, like reading from files, output configuration, doing exclusions, etc.
But now it’s time for what you probably came here for—which is a list of tactical examples based on common use cases.
Finding Company Properties
The substring bit is important. Too much text and you miss it, not enough and you get tons of false positives.
A common way to start is by searching for substrings of the company, to see what all subdivisions they might have around the world. And don’t forget to search for companies they’ve acquired or merged with as well.
amass intel -org uber
New Domains via CIDR
One way to find new domains is to look by CIDR range.
amass intel -ip -cidr 104.154.0.0/15
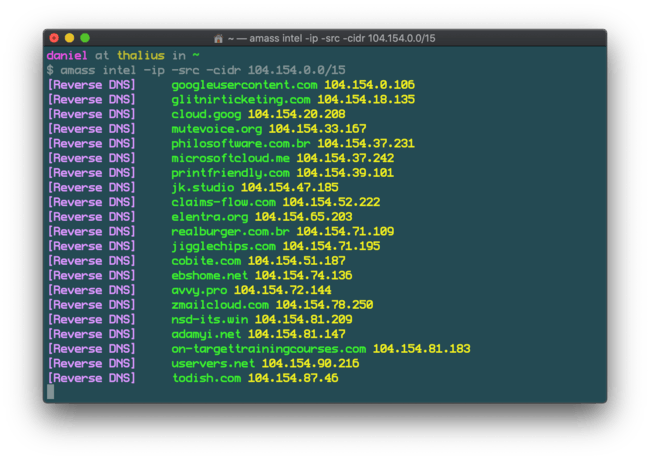
Finding domains hosted on a CIDR range
New Domains via ASN
Another way to find new domains is to look by ASN.
amass intel -asn 63086
Finding Subdomains
Once you have a good list of domains, you can start looking for subdomains using the enum subcommand.
amass enum -d -ip -src danielmiessler.com
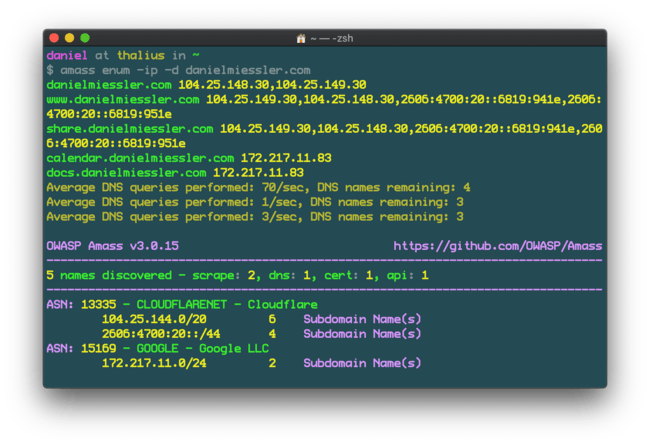
With the IP option showing IPS for discovered domains
Summary
amass is a powerful tool that helps both attackers and defenders improve their game. It’s possible to find one-off tools that might do some of these functions better, but such tools often decay quickly into obsolescence.
It’s quite nice to have a solid, well-organized tool that can do most of what we need from a single place.
Watch out for more in this series on recon-related tooling, and in the meantime you can check out my other technical tutorials >.
Stay curious!
Notes
If you have any favorite functionality you’d like to include, reach out to me here >.