Wireless: WPA2 Enterprise Integration With Active Directory 2008 Using NPS
So I finally got my Wireless Access Point (an Apple AirPort) authenticating off of Active Directory-integrated LDAP in Server 2008 (which is called NPS now). So now I authenticate wireless users individually, through Active Directory, rather than using a shared secret. WPA2 Enterprise…it overfloweth with w00tn3ss.
Setup
So here are the basic steps, and I can provide more detail if you have questions in the comments.
1. Install AD and Create Users
First install Active Directory. Easy stuff.
Next, since the whole point of this is to have unique user authentication, you need to have…users. So create them as usual but be sure to add them to a new group like "RADIUS" or something, and ensure that they have dial-in access within their user account. I used "RADIUS Users" because I’m creative and eccentric.
2. Enable Network Policy and Access Services in Server 2008
This is what replaces IAS in Server 2008. The install is pretty straight forward; it’s the policy that’s the trick.
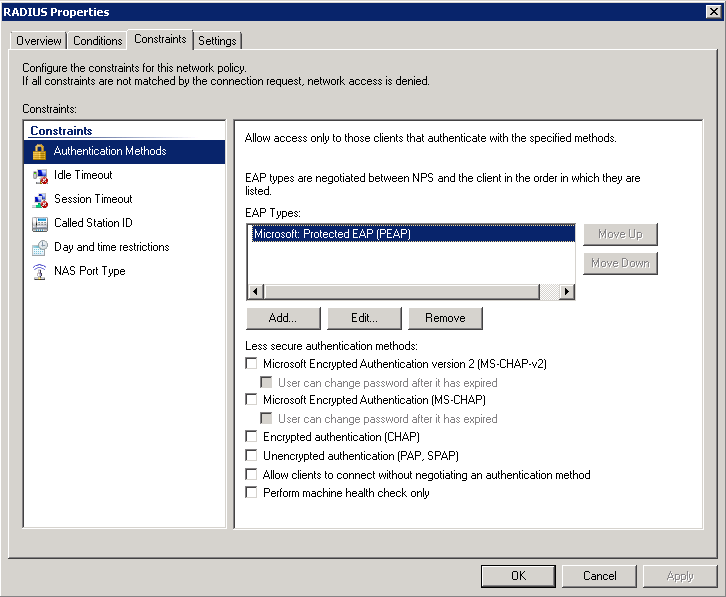
I’m using PEAP right now, although I haven’t yet researched the ideal setup. Soon, though, and if you have any input (or good reading) on this let me know.
You also want to set the authentication rule to Windows Authentication within the policy, and then select your group out of Active Directory that you placed your users in.
Be sure to setup a RADIUS client within the NPS configuration, and enter the info for your access point rather than for your individual clients.
3. Configure Your Wireless Access Point
Tell your wireless access point to use WPA2 Enterprise, and configure the RADIUS info to point to your domain controller that you just set up NPS on. Enter the shared secret you configured during the NPS piece.
4. Configure Your Clients
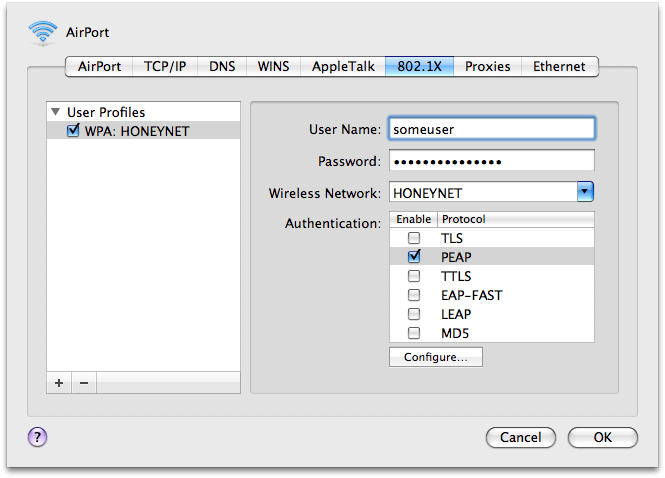
Connect to your AP as you normally would, and when prompted you will enter your Active Directory username and password. I’ve chosen PEAP as my authentication protocol pending more research on which is ideal:
Fin
And that’s about it. Connect to your AP and enter your credentials.
Now when your friends come over you simply make them an account in Active Directory and they have wireless access using their own username and password. And when they leave you disable their account until next time. This way you get all the added benefits of password expiration and stuff like that.
Oh, and if any part of this fails, check the NPS logs on your DC. Logs are much improved in 2008 vs. previous versions of Windows, and it’s pretty easy to troubleshoot. I saw a lot of errors with authentication types not being supported before I figured out which to use.
Bonus: If you’re one of the cool kids you’ll have your AD and AP logs going into Splunk > so you can see (and alert on) attempts to access your wireless network from accounts and MAC addresses you don’t recognize. More on that later.
Anyway, enjoy, and hit me up with any questions. ::