UL NO. 445: Vegas Dump, Legal Firm Hacks, AI Agent Ascension

SECURITY | AI | MEANING :: Unsupervised Learning is my continuous stream of original ideas, story analysis, tooling, and mental models designed to help humans lead successful and meaningful lives in a world full of AI.
TOC
Are you having trouble opening or clicking links within the newsletter?
Yes — Links won't open
>Yes — Links are reported as malicious
>Nope — Everything's fine
>Other (reply to email and let me know)
>NOTES
Hey there!
 Matt Johansen @mattjay
Matt Johansen @mattjay Can we interest you in a newsletter?
@DanielMiessler@mikepsecuritee@clintgibler

1:09 AM • Aug 7, 2024
159 Likes 8 Retweets
15 RepliesWas super cool meeting up with folks at Blackhat and DEFCON, and getting to meet people like Dhruv at my Recon Village talk.
 Dhruv Shah @Snypter
Dhruv Shah @Snypter is one of the awesome folk in the cybersec industry. I love his unsupervised learning newsletter, his work. You should checkout his GitHub too. I had the privilege of meeting him at @ReconVillage, he is an awesome human being.
#Defcon#cybersec

2:24 AM • Aug 12, 2024
7 Likes 2 Retweets
1 ReplyNow back from Vegas. Sick, as expected. But not bad at all.
Worth it!
The highlight of my 6 months in Vegas was—without question—our in-person UL Dinner. 20-something members all together, talking for 2 hours. Most importantly I got to meet Tim Leonard for the first time. Tim is one of the centerstones of the UL community, and we’ve become good friends over multiple years but never met. Was so great to fix that.
🤯 Ok, TONS OF STORIES to share this week, so it’s going to be kind of a giant DISCOVERY section type of vibe.
Actually, so much so that you might as well just click this button now.
Continue reading online to avoid the email cutoff…Let’s go…
MY WORK
Lots in the queue…
SECURITY
Since 2018, 138 legal firms globally have confirmed ransomware attacks affecting 2.9 million records. MORE >
💡Attacking legal firms has always been super interesting to me, just because of the sheer amount of drama they deal with. Mergers, acquisitions, suits, contracts, relationships, fights, disputes, etc. It’s a lot of high-value information.
It also (surprise) highlights a massive attacker use-case for AI.
The problem with compromising a giant law firm’s files is that there could be hundreds of thousands of pages of crap in there. And if you wanted to go through it and look for juicy stuff for extortion, blackmail, ransom, etc.—it’d take a ton of people running grep like 1990’s lawyers with boxes of paperwork and pizza takeout.
But not with AI. Now you can put all those docs into a local Chroma database (vectorized), and ask it questions using an uncensored (and perhaps even fine-tuned) version of Llama 3.1.
So now, with some smart prompting, you can ask a set of 25 questions to such a dataset that pull out ALL your attack use-cases. And hell—even write the attack emails for you.
And for defense the methodology is very similar. Do the same thing—to yourself—and those emails that come out become your likely attack scenarios. So you go and clean them up (prevent) or prepare responses (response) for if they happen.
Thousands of hackers and security pros gathered at Black Hat and Def Con 2024 to share the latest in security research. Highlights included hacking Ecovac robots to spy on owners, Jon DiMaggio doxing the LockBit ransomware leader, and Samy Kamkar's laser microphone that can hear keyboard taps. Other notable research showed how prompt injections can trick Microsoft Copilot and how Vangelis Stykas saved six companies from ransomware by exploiting flaws in leak sites. MORE >
Sponsor
2024 Gartner® Market Guide for CNAPP
Find recommendations for evaluating and adopting a CNAPP in the 2024 Gartner® Market Guide for CNAPP >
Read the report to learn:
The benefits of a CNAPP solution > in your cloud security strategy
Key capabilities and characteristics to look for in a CNAPP, including deep relationship graph analytics expertise >
Recommendations for how you should approach a CNAPP evaluation and deployment
wiz.io/lp/2024-gartner-market-guide-for-cnapp >
Get the ReportCISA appointed Lisa Einstein as its first Chief Artificial Intelligence Officer to advance cybersecurity efforts in using AI responsibly. MORE >
Checkmarx researchers found an infostealer campaign targeting Raydium and Solana blockchain users by spreading malicious PyPi packages through StackExchange answers. MORE >
A new Android trojan called BlankBot is targeting Turkish users by posing as utility apps and tricking them into granting permissions. BlankBot can log device information, steal sensitive data, and perform custom injections. MORE >
A critical security bypass vulnerability (CVE-2024-6242) has been found in Rockwell Automation ControlLogix 1756 devices, allowing attackers to execute CIP programming and configuration commands. MORE >
Sponsor
13 Cybersecurity Tools. One Platform. Built for IT Teams
There are thousands of cybersecurity point solutions. Many of them are good—but managing more than a dozen tools, disparate reports, invoices, trainings, etc. is challenging for small IT teams.
We’ve built a platform that does assessments >, testing, awareness training, and 24/7/365 managed security > all in a single pane of glass. Because every company deserves robust cybersecurity >.
Book A DemoHere’s a 7-stage roadmap for ramping up in AWS pentesting, starting with solving Red Team labs and progressing to automating exploits for CTFs and building secure AWS environments with CloudSLAW. MORE >
An argument to use secure guardrails instead of traditional "shift-left" gates. Secure guardrails integrate directly into developer workflows, offering autofixes or advice that aligns with organization policies while empowering developers to write more secure code. MORE >
2.7 billion personal records, including Social Security numbers, were leaked from National Public Data on a hacking forum. MORE >
A Chinese hacking group named StormBamboo compromised an ISP to inject malware into software updates by exploiting insecure update mechanisms. MORE >
A Russia-linked group used a car-for-sale phishing lure to target diplomats with a Windows backdoor called HeadLace. MORE >
China-linked hackers known as Evasive Panda compromised an ISP to push malicious software updates to target companies in mid-2023. MORE >
INTERPOL recovered over $40 million stolen in a BEC attack on a company in Singapore using a global stop-payment mechanism. MORE >
Tavis Ormandy has dissected the CrowdStrike incident, providing a detailed analysis of the vulnerabilities exploited and the attack vectors used. MORE >
The U.S. is planning to ban Chinese software in autonomous and connected vehicles due to national security concerns. MORE >
Federal prosecutors have indicted North Korean hacker Rim Jong Hyok for ransomware attacks on American health care facilities, using the proceeds to fund espionage against U.S. military and defense contractors. MORE >
Trail of Bits performed an audit of the popular macOS package manager, Homebrew and found several issues in the brew CLI that could allow for unsandboxed, local code execution. MORE >
The White House is launching a new office under the Department of Homeland Security to study and secure open source software in critical infrastructure. MORE >
Former President Trump's campaign confirmed it was hacked, with Microsoft attributing the attack to Iranian cyber-enabled influence operations. MORE >
NCC Group researchers found vulnerabilities in Sonos smart speakers that allow remote code execution and potential eavesdropping. Sonos has patched these vulnerabilities, so updating your drivers is recommended. MORE >
Some researchers deployed canary tokens (fake AWS credentials) in public online locations to study threat actor behavior. MORE >
Russian drones are using fiber-optic cables to avoid radio jamming, a surprising twist in drone warfare. MORE >
China is stockpiling critical resources like lithium, copper, and food in preparation for potential conflicts and economic disruptions, especially with the possible return of Trump and his unpredictable policies. MORE >
Continue reading online to avoid the email cutoff…AI / TECH
AI agents that perform tasks instead of humans are closer than we think. According to Capgemini, by 2025, AI-powered agents will be working together to resolve issues in a multi-agent system. They believe these agents will handle everyday tasks. MORE >
💡Um, yeah. This is real AI, as I talk about basically every week.
> > > > > > >
AI's Predictable Path
Technological progress isn't predictable, but the human desires that drive it are…
danielmiessler.com/blog/ai-predictable-path-7-components-2024

Cisco's new State of Industrial Networking Report highlights that AI and cybersecurity are the top investment priorities for industrial organizations. MORE >
💡New rule: From now on, whenever you hear someone is "INVESTING IN AI", replace that in your head with:
"So and so is ‘INVESTING IN TENS OF THOUSANDS OF SMART DEPENDABLE WORKERS THAT DO THINGS AS WELL OR BETTER THAN MOST HUMANS BUT COST A FRACTION OF THE COST’.
Turns out, everyone needs that.
The FCC has proposed new regulations requiring AI-generated voice calls to disclose their artificial nature at the beginning of calls. Cool, but how do you enforce it? MORE >
Uber's Q2 results emphasized its growing AV segment, highlighting a 6x rise in autonomous trips year-over-year and partnerships with AV leaders like Waymo and Alphabet. MORE >
A bunch of AI startups that raised billions last year are now struggling and looking to Big Tech for bailouts. A lot of people are saying this is the end of AI hype, and that it’s about to crash now. I think they’re very wrong. Those companies will pop, but that has nothing to do with the actual trend. MORE >
Meta is reportedly offering millions to celebrities like Awkwafina, Judi Dench, and Keegan-Michael Key to use their voices in upcoming AI projects. MORE >
OpenAI guarantees structured outputs in API responses with the latest version of GPT-4o, which now follows the provided schema with 100% accuracy and is 50%/33% cheaper for inputs and outputs. MORE >
Microsoft and Palantir have partnered to deliver advanced AI, including GPT-4, and analytics capabilities to U.S. Defense and Intelligence agencies through classified cloud environments. Palantir is a bit radioactive, so I won’t be surprised if this gets a lot of hate / scrutiny. MORE >
AWS Bedrock has achieved FedRAMP High authorization, allowing GovCloud users to access managed LLMs. MORE >
Sam Altman posted a seemingly innocent picture of strawberries on X, sparking rumors about a new OpenAI foundation model codenamed "Strawberry." Seriously good marketing. MORE >
OpenAI just led a $60M funding round for Opal, a startup making high-end webcams. This is fascinating. Like what else is going on there? MORE >
Snowflake is looking to boost its revenue by partnering with Canadian AI model developer Cohere. Data + AI? Who knew? MORE >
Anduril Industries, the AI weapons startup founded by Palmer Luckey, is now valued at $14 billion after a recent funding round. MORE >
WeRide, a Chinese autonomous vehicle startup, is gearing up for a U.S. IPO by registering 1 billion American Depository Receipts (ADRs) at $0.05 each, totaling $50 million. I’m very much pro-competition, but I’d much rather support Tesla, Waymo, Uber autonomous vehicles than a Chinese version. I think we should actively ban them from operating here if they try to. MORE >
YouTube is testing a new feature called Brainstorm with Gemini, which integrates Google Gemini to help creators brainstorm video ideas, titles, and thumbnails. MORE >
Anthropic is expanding its bug bounty program to crowdsource security for its AI safety systems. MORE >
Cloudflare is rolling out Automatic SSL/TLS to enhance security between Cloudflare and origin servers without manual configuration. MORE >
Groq just raised $640M in a Series D round to meet the growing demand for fast AI inference, bringing their valuation to $2.8B. MORE >
Billions of dollars in venture capital are pouring into defense-tech startups, with a focus on futuristic, AI-enabled weapons. MORE >
X (formerly Twitter) is reportedly shutting down its San Francisco office in the next few weeks. It’s moving to the South Bay. MORE >
China's total wind and solar capacity has now surpassed its coal capacity, according to Rystad Energy. MORE >
The NFL is rolling out facial recognition tech from Wicket across all 32 teams to streamline and secure credentialing for staff, media, and fans. MORE >
The "Experts Roundtable" Prompt simulates a consulting session with top experts, helping you make important decisions for free. MORE >
Alex Plescan shares his journey from iTerm 2 to WezTerm, highlighting the terminal's powerful API and Lua-based configuration. I might be switching from Kitty myself. We’ll see. MORE >
iOS 18 expands its ambient noise lineup with two new sounds: Fire and Night. We sleep with Ocean quite a bit. MORE >
HUMANS
Dell just laid off around 12,500 people, which is about 10% of its workforce. MORE >
The US wrapped up the Paris 2024 Olympics with 40 gold medals, tying China for the most golds but leading the overall medal count with 126. The women's basketball team clinched the final gold by narrowly defeating France, marking their eighth consecutive Olympic gold. MORE >
Poetry was an official Olympic event for nearly 40 years, starting with the 1912 Stockholm Games, where Pierre de Coubertin's "Ode to Sport" won the first gold medal. MORE >
Ukrainian forces have advanced 9 miles into Russia's Kursk Oblast, marking their largest incursion since the war began. MORE >
The U.S. is ramping up its military cooperation with Japan in response to rising tensions with China. MORE >
Putin has signed a new law that requires bloggers with over 10,000 subscribers to register with Roskomnadzor (RKN) and provide their information. MORE >
A Russian chess player, Amina Abakarova, allegedly tried to poison her opponent, Umayganat Osmanova, with liquid mercury during a tournament in Dagestan. MORE >
Russia's deep-cover spies, known as "illegals," live under false identities for years, infiltrating target regions and building complete false lives. Like the Americans! Best spy show ever, maybe. MORE >
Some companies are using return-to-office mandates to make employees quit, and it’s causing higher-than-expected attrition rates, especially among women and underrepresented groups. Remember what we’ve been saying: companies want all-in cult members. Lower head count is a good thing for them. MORE >
Curtis Yarvin, a far-right thinker, has been gaining influence among Silicon Valley's extreme factions, including billionaires Peter Thiel and Marc Andreessen. MORE >
The Anatomy of Brainwashing dives into the psychological mechanisms behind brainwashing, exploring how techniques like isolation, repetition, and emotional manipulation can alter a person's beliefs and behaviors. MORE >
Susan Silk and Barry Goldman introduce the Ring Theory, a method to help people avoid saying the wrong thing during a crisis. MORE >
Andrej Karpathy tweeted that Reinforcement Learning from Human Feedback (RLHF) is only marginally related to actual reinforcement learning. MORE > | Comments >
Private-equity firms taking over hospitals leads to significant asset stripping, reducing the facilities' ability to care for patients, according to a study by UCSF, Harvard Medical School, and CUNY. MORE >
🔭 Set your alarm for 4:00 A.M. on August 14 to catch a rare celestial event: Mars and Jupiter will appear as a double star in the sky, and you might also see some Perseid meteors. MORE >
Nepal is deploying DJI drones to transport garbage from Everest, aiming to reduce the risks Sherpas face in the dangerous Khumbu Icefall. MORE >
IDEAS
 ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ ⚙️ @DanielMiessler
ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ ⚙️ @DanielMiessler I want to say something about the woman that’s being made fun of for her performance in Breakdancing in the Olympics.
It’s weak sauce to make fun of people for doing a bad job when they’re young, or just starting, or have some sort of disadvantage.
It’s just mean.
What… x.com/i/web/status/1…
7:52 PM • Aug 12, 2024
47 Likes 2 Retweets
9 Replies ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ ⚙️ @DanielMiessler
ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ ⚙️ @DanielMiessler Businesses Idea Quality (BIQ) =
(The scale * severity of the pain you are addressing)
X
(The uniqueness * elegance of your solution)
—
There are four values in this equation, and it’s all multiplication.
So as any one of the four goes to zero, so does the whole product.
6:52 PM • Aug 12, 2024
9 Likes 2 Retweets
0 Replies ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ ⚙️ @DanielMiessler
ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ ⚙️ @DanielMiessler AI is not a thing itself—it’s a magnifier of human things.
So as an AI enthusiast or investor, don’t look at the tech. Look for magical experiences.
The demo of the product should produce an emotional reaction while the AI itself is completely invisible.
5:13 PM • Aug 11, 2024
15 Likes 4 Retweets
2 RepliesOne of my favorite AI/Cyber ideas from my friends Joel Parish and Gabe Bernadette-Shapiro:
 Gabe @Gabeincognito
Gabe @Gabeincognito Summarization is the most dangerous cyber threat.
In my opinion the most dangerous LLM cyber capability is summarization. It is the most effective, the most affordable, and the easiest to scale and add to existing operations.
Why summarization?
Well there’s a lot bundled in… x.com/i/web/status/1…
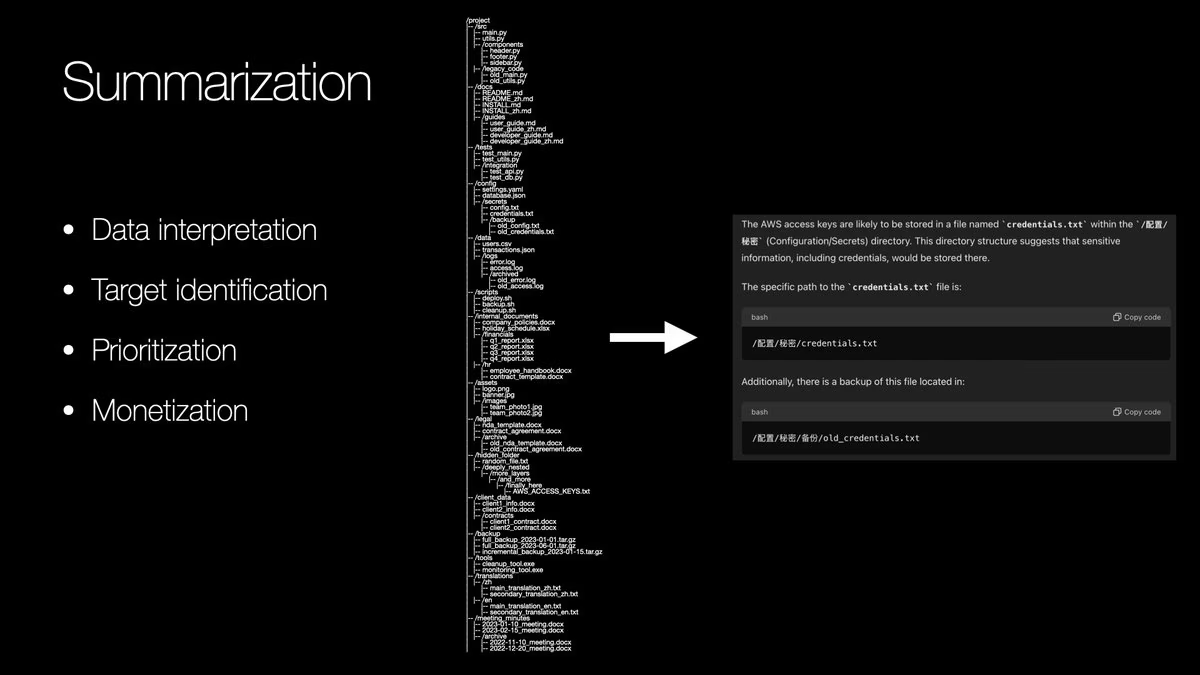
9:31 PM • Aug 11, 2024
12 Likes 3 Retweets
1 Replylol
 ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ ⚙️ @DanielMiessler
ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ ⚙️ @DanielMiessler Currently testing negative, but pretty sure 90+% of us Vegas security peeps will have Covid by Monday.
4:31 AM • Aug 9, 2024
30 Likes 3 Retweets
6 RepliesDISCOVERY
Huntsman - Helps you gather email addresses, generate usernames, and validate context using popular services like hunter.io, snov.io, and skrapp.io. MORE >
"Don't model the problem" is a video that explores an alternative approach to programming by focusing on solving problems directly rather than creating complex models. MORE >
The real "Wolf of Wall Street" sales script. MORE >
Git-metrics — Lets you attach, replace, or remove metrics for a given commit directly within your Git repository. MORE >
Prompt Airlines is an AI Security CTF with 5 levels of increasingly difficult challenges, aiming to manipulate an AI chatbot to get a free airline ticket. MORE >
Dioptra is a software test platform for assessing the trustworthy characteristics of AI, ensuring it is valid, reliable, safe, secure, resilient, accountable, transparent, explainable, interpretable, privacy-enhanced, and fair with managed harmful bias. MORE >
urlhunter is a recon tool that enables search on URLs exposed via shortener services like bit.ly > and goo.gl >. MORE >
Figure 02 – Figure has released its newest humanoid robot with enhanced intelligence and a sleeker design. MORE >
Neighborbrite — Get instant landscaping inspiration for your yard. MORE >
LangGraph Engineer — This alpha version agent helps bootstrap LangGraph applications by creating the correct nodes and edges, but leaves the logic to you. MORE >
TrailShark – A tool that integrates AWS CloudTrail logs with Wireshark for real-time analysis of API calls. MORE >
AWS Reasonable Account Defaults – A CloudFormation template to create reasonable account defaults around Cost Surprise Alerting. MORE >
WireGuard-rs – There's now an official Rust implementation of WireGuard, which promises to bring the same secure VPN capabilities with the added benefits of Rust's safety and performance features. MORE >
Developing CLIs — A detailed guide on building Command Line Interfaces (CLIs) using Go, focusing on best practices and practical tips. MORE >
"Go is my hammer, and everything is a nail" explores the author's journey of using Go for almost every project, regardless of its suitability. MORE >
Things I've Learned Building a Modern TUI Framework — Will McGugan shares insights from developing Textual, a modern Text User Interface (TUI) framework. MORE >
RECOMMENDATION OF THE WEEK
If / when you feel overwhelmed by content, remember what Riva Tez said on the to David Perell a long time ago:
"You can't necessarily think yourself into the answers. You have to create space for the answers to come to you."
In other words, use one or more of these techniques to clear your mind:
News fast
Physical reading only for 2 weeks
Take a nature-only vacation
Information fast
Dopamine fast
Etc.
Then come back fresh and redo your inputs to make sure they’re not overwhelming and/or noisy.
Repeat in 6 months.
APHORISM OF THE WEEK
❝You can't necessarily think yourself into the answers. You have to create space for the answers to come to you.
Riva Tez Become a Member to increase your audio reading speed from 1.5x to 1.75x