A Simple Framework for Being Anti-Fragile
Three things you need to thrive in a world that keeps changing
This is some of my favorite, most popular, and latest content. You can also browse and search the archives.
Three things you need to thrive in a world that keeps changing
Pursuing the unbelievably exciting goal of making everything verifiable
Small things can really make your AI system more enjoyable to use
2026 might be the year continuous algorithm approaches start to generalize into universal problem solvers
Even if Claude Code were the actual addiction, it would still be better than porn, TikTok, and Netflix

Looking back at my predictions to see what I got right, wrong, and what's still playing out
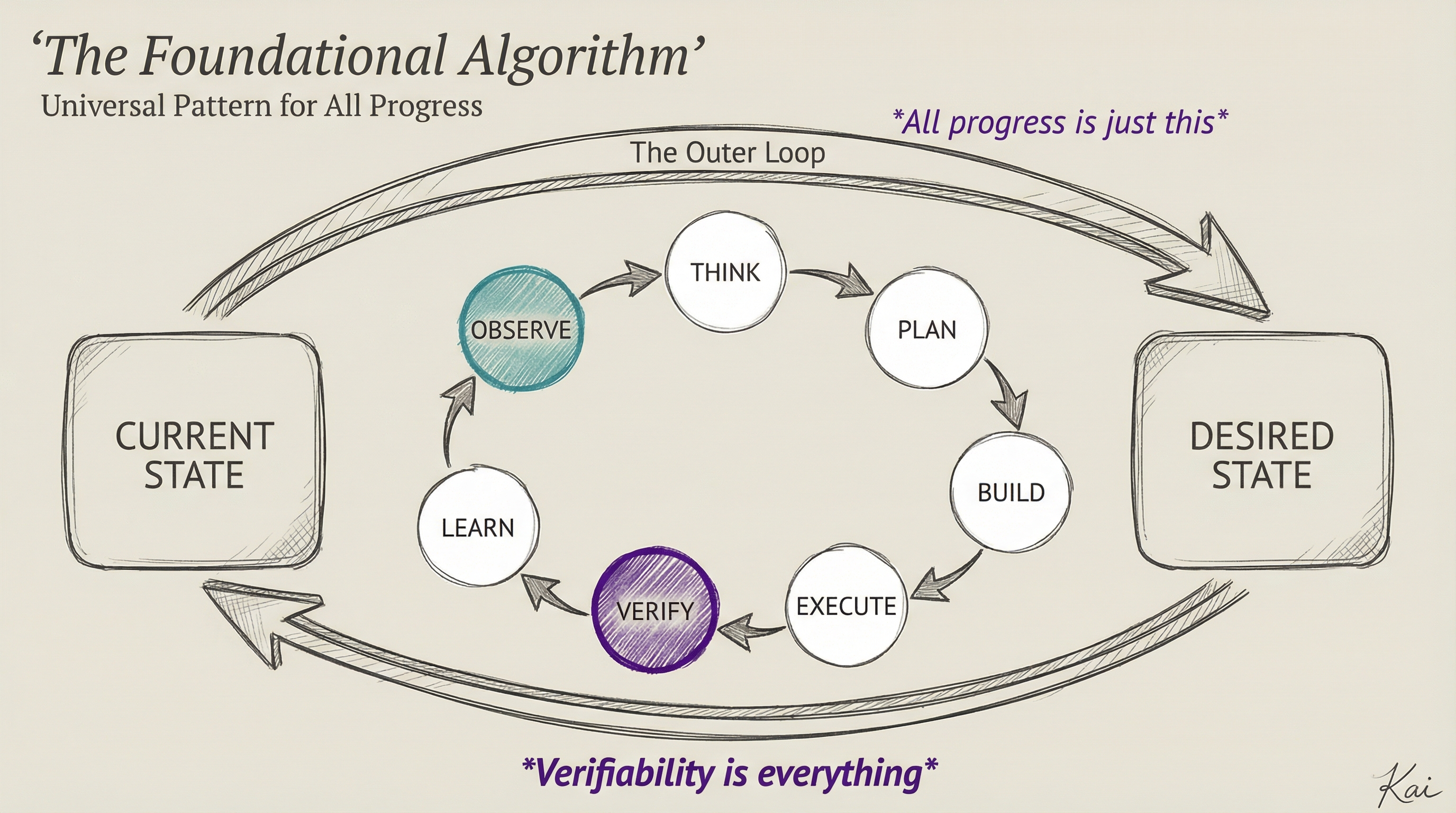
My thoughts on what's coming for AI in 2026

My thoughts on what's coming for Cybersecurity in 2026