Security Report Analysis: 2018 DBIR Report
In this Security Report Analysis (SRA) series I look at various security reports and pull out the main points.
This doesn’t replace a complete and detailed read of these reports, but it exposes you to some of the key takeaways that you might not otherwise have seen.
REPORT: The 2018 DBIR Report >
Key points
These points are a combination of the report’s actual points combined with my own interpretation of them. Some of the analysis is not theirs, in other words. Don’t take this as me putting words in their mouths, but rather me trying to parse and interpret for my and your benefit.
This year’s report covers 53,308 security incidents, 2,216 data breaches, 65 countries, 67 contributors
More of the same: same attacks are still working because same weaknesses still exist
73% attacks were outsiders
12% attacks were nation states
Financial was the lead motive, followed by Espionage
Errors were 17% of breaches
The top malware type was ransomware (39%)
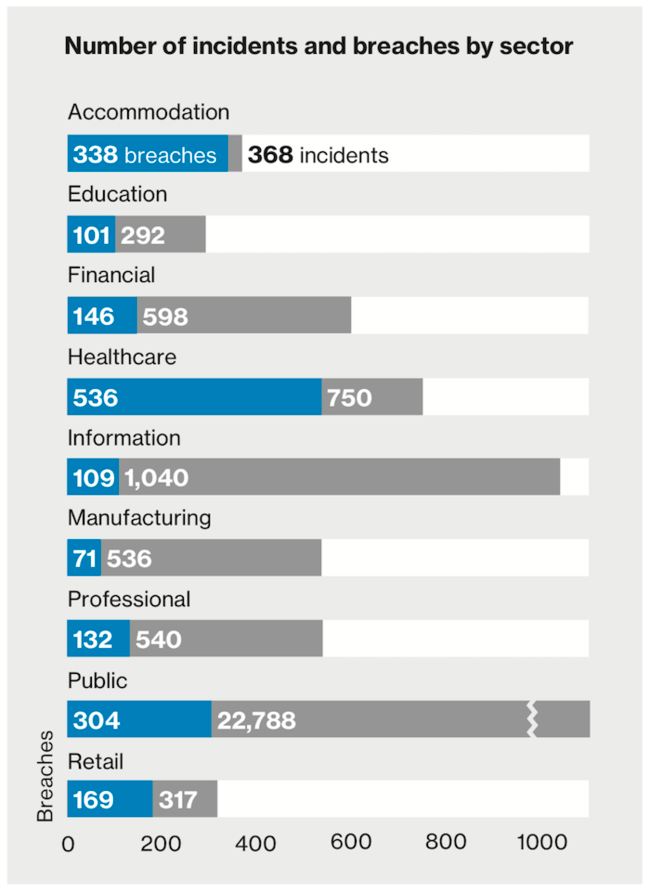
90% of accommodation industry breaches involved POS systems
Healthcare is the only industry where insider threat is greater than outside (56%)
In the public sector (government), Espionage was the motive in 44% of cases
Most attacks across industries are opportunistic, but in Manufacturing 88% are targeted
The Information and Retail sectors were most plagued by web application attacks
66% of breaches took months or longer to discover
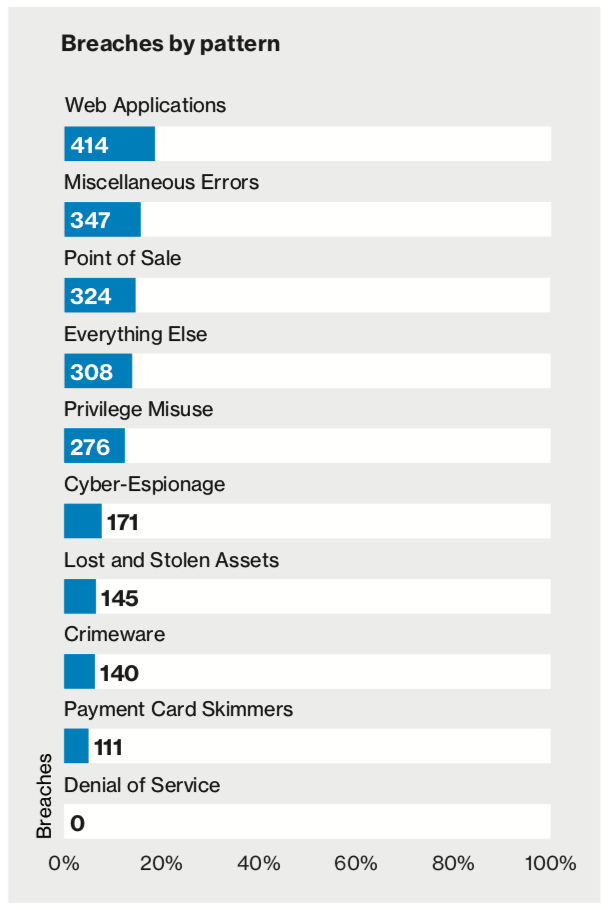
94% of security incidents and 90% of confirmed data breaches fall into DBIR’s nine incident classification patterns across all years
DBIR recommendations
Be vigilant
Make people your first line of defense
Only keep data on a need-to-know basis
Patch promptly
Encrypt sensitive data
Use two-factor authentication
Don’t forget physical security
My analysis
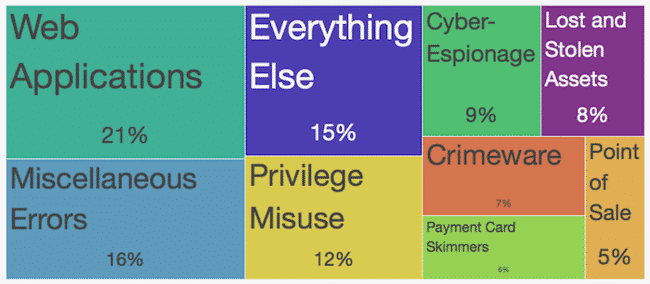
The top two issues that resulted in breaches (not just incidents) were Web Application Attacks and Miscellaneous Errors. I find that fascinating and familiar.
The recommendations from DBIR don’t seem right to me.
For web apps that means:
Finding all your web applications
Performing regular vulnerability assessments on them
Remediating issues such as SQli, L/RFI that can cause the difference between a breach and an incident.
Check out Jeremiah Grossman’s essay on this topic >.
I think there should be more focus on the acute problems causing the first n most likely causes of breaches, because not all vulnerabilities lead to losses in equal proportion.
I launched a service called Helios > that addresses this problem directly.
For Miscellaneous Errors, you need to be watching your environment continuously, and ensuring that if something moves into an undesired state, you’ll know about it immediately.
Spending money on threat intelligence when you don’t have asset management and monitoring is like being 100 pounds overweight from cheeseburgers and dumping money into multivitamins instead of reducing calories and exercising.
There is just too much focus on edge cases in our industry. It’s not usually the 0-day that’s going to get you, or North Korea. It’s the admin portal that’s been sitting out there for weeks without you knowing. It’s the websites you didn’t know about that are running two-year-old unpatched frameworks. It’s the EC2 boxes that have Mongo on them full of your data with no credentials. And unprotected S3 buckets.
It’s the big stuff.
Work on that first.
—
Anyway, another stellar report from Verizon. I think this report should be an InfoSec Event every time it’s released.
The week it comes out, every infosec team should take a day out of meetings and go through the results to see if they should adjust any of their priorities.
REPORT: The 2018 DBIR Report >
Notes
While this capture can be helpful, I suggest reading the whole report for full context. The writing was remarkably easy to move through.
The interactive version of the report was quite strong as well. Link >