Security Log Analysis: August 2017
I was just watching some server logs and decided to pull some statistics on common attacks from Snort and Bro.
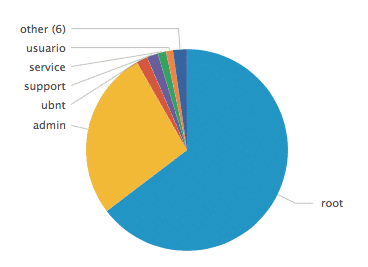
This first one is SSH bruteforce attempts.
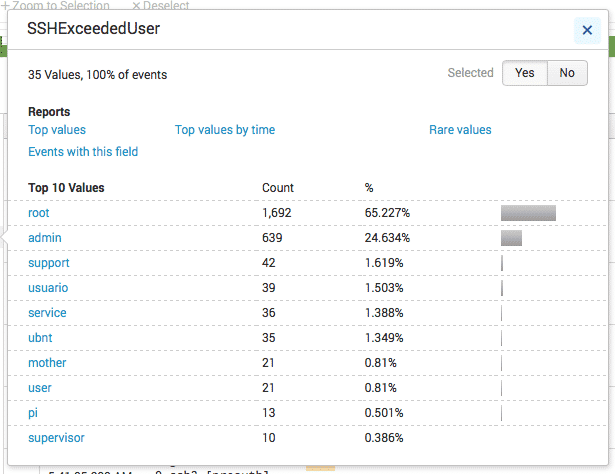
Here are the most commonly attempted usernames:
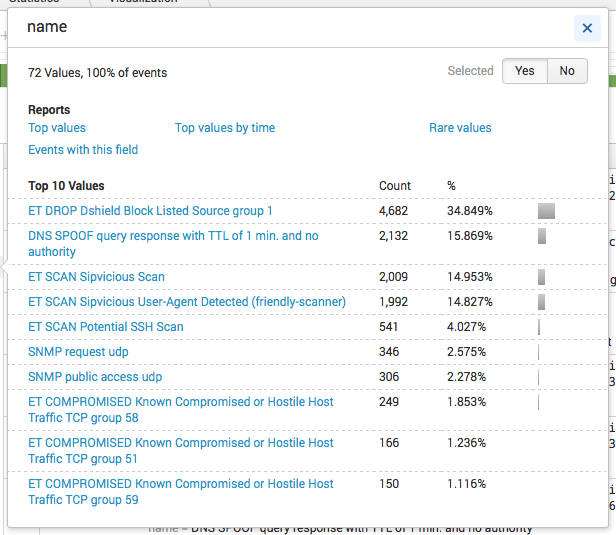
Here are the most common IDS alerts at Priority 2.
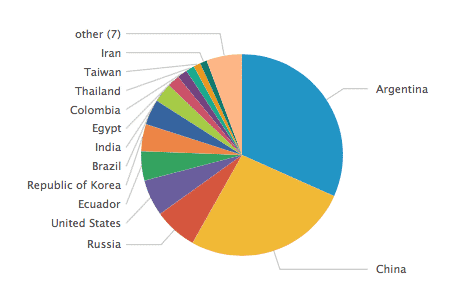
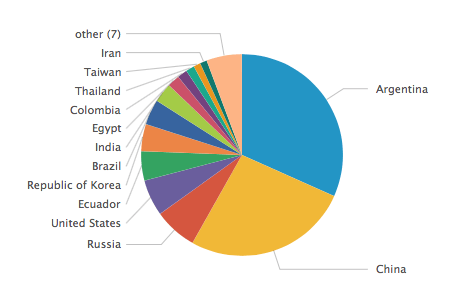
These are the most common source countries for IDS attacks.
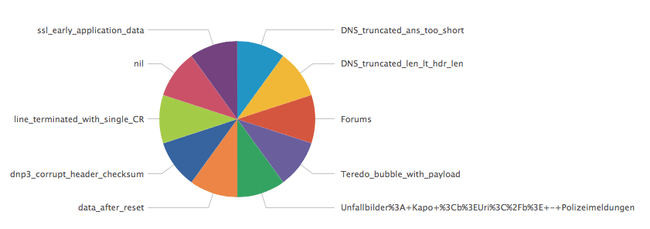
And here are the 10 least common issues captured by Bro.
I also have live alerts set up for several types of event, such as bruteforce attempts against services, access to honey content, etc.
Knowledge of what’s happening on your servers is crucial to both defense and general curiosity.
If you’re not collecting data from your servers for edification purposes, you’re missing out on a rich stream of opportunities to learn about a great many things. Who’s attacking you, how, what they’re attacking, how common tools work, etc.
Capture, Watch, Improve.