Some Quick Takeaways from the 2017 Verizon DBIR
For those who lack the time to read the entire report, here are some of the key findings along with some comments.
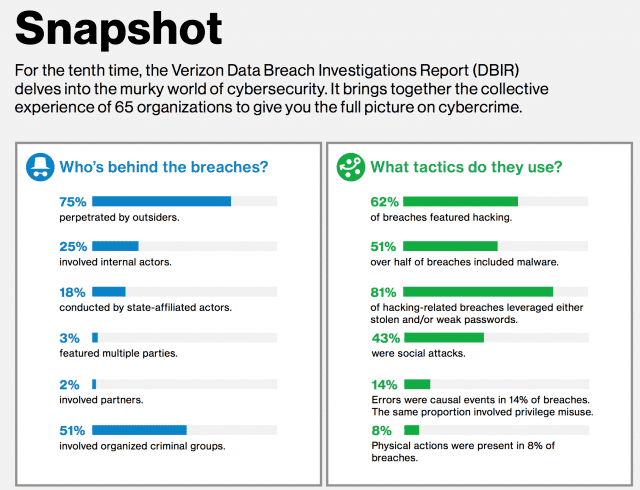
Attackers
75% of breaches done by outsiders.
25% involved internal actors.
18% state actors.
51% involved organized crime actors.
I see 25% involving internal actors as quite high, but that depends on the definition of "involved".
Targets
24% of breaches affected financial organizations
15% of breaches affected healthcare
Public sector were third at 12%
Retail and hospitality combined for another 15% of breaches.
Tactics
62% of breaches used "hacking"
51% of breaches used malware
81% leveraged stolen/weak passwords
43% were social engineering based
What does "hacking" mean? And how much hacking did or did not involve malware?
Other findings
66% of malware got in via email
73% of breaches were financially motivated
21% of breaches were espionage related
27% were discovered by third parties
Analysis
I find the 1/4 insider involvement to be high. Not saying it’s wrong. Just saying it seems high.
I think they could use a better term than "hacking" to describe their most common type of tactic. Perhaps "manual intervention"?
I’d love to see some sort of analysis of controls in this report, or a similar report. So basically what controls from say the CIS set are most recommended this year based on the DBIR findings?
That’s not a bullseye because every company is different, but maybe they could do a recommended controls list for each industry or something.
Anyway, solid stuff as usual from he team. And I enjoyed the summary as well.
Notes
I imagine a lot of these questions were answered in the full version of the report. This is analysis of the executive summary.