Stop Trying to Violently Separate Privacy and Security
I just stumbled upon an article by Mark R. Heckman, Ph.D, CISSP, CISA that—like so many others in the industry—wildly contorts himself to make a distinction between security and privacy. He writes:
I argued here > why I don’t think this difference matters as much as people think.
Without a clear understanding of the difference, data security and privacy is often conflated in ambiguous and imprecise policies.
Mark R. Heckman
Mark R. HeckmanHe then goes on to give some definitions: first from the International Association of Privacy Professionals (IAPP):
Data privacy is focused on the use and governance of personal data— things like putting policies in place to ensure that consumers’ personal information is being collected, shared and used in appropriate ways. Data security focuses more on protecting data from malicious attacks and the exploitation of stolen data for profit. While security is necessary for protecting data, it is not sufficient for addressing privacy.
IAPP
IAPPThen he gives what he calls a better definition, from the US Department of Health:
The Privacy Rule sets the standards for, among other things, who may have access to PHI, while the Security Rule sets the standards for ensuring that only those who should have access to EPHI will actually have access.
US Department of Health
US Department of HealthHe’s using both definitions to set up his ultimate argument, which is that:
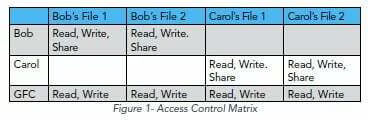
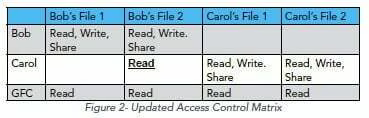
Data Security is enforcement of the authorized access rights currently in the access table, and Privacy is a policy on control over where and when authorized access rights appear in the table.
And he provides some tables to illustrate this.
And finally he goes on to say:
Privacy is not the state of information being protected from unauthorized access. Information is not private because unauthorized users are prevented from accessing the data, but it is secure. People frequently conflate confidentiality – the property that only authorized users can read protected information – with privacy. But as the access control matrix model clearly shows, confidentiality is a security policy.
Professor Mark R. Heckman
Professor Mark R. HeckmanI have to say, I find this truly perplexing. Especially coming from a professor, with a Ph.D, who’s been in security for 30 years.
What exactly is the obsession with drawing such a bright line between these things?
There is clearly some kind of difference between Security and Privacy, but there are also differences between being a firewall engineer and an endpoint security specialist. Same with being a red-teamer vs. a compliance person.
These are all different things, but they’re all part of cybersecurity / information security.
Why is that?
Let’s look at the definitions of information security.
Hmm, so, the prevention of unauthorized access, use, and disclosure of information? Do we need to look up what unauthorized means? I think it means people accessing or using a given set of data that aren’t supposed to.
Does that remind you of anything?
Professor Heckman is essentially arguing for a massive separation between these two terms, so that this can be spelled out in separate policies—all because there is evidently some sort of tangible problem today being caused by their conflation.
I’ve never seen that in my 20 years of consulting.
I’ve never seen a single person be confused by what it means to protect sensitive data. It’s common sense. The problem that companies actually have is not knowing where their data is, who has it, what its classification is, who has access to it, etc. It’s a data inventory problem, not an issue with confusing security and privacy.
Information Security means protecting data from unauthorized access and use, and privacy means ensuring that only authorized people can have access to peoples’ private data. Kind of similar, right?
These are not any different than database security vs. filesystem security, or firewall people vs. WAF people, or incident response people vs. compliance people.
You can have specialization within a field without needing to call it a different species altogether, and Privacy specialists are a good example of that.
Do they have different skillsets? Sure. Do they take different training? Sure. Go to different conferences? Fine. But are they fundamentally doing different things? Is one in security while the other isn’t?
No.
The final (and worst) point in his argument is that information is Secure when it’s protected according to policy, but that it’s Private when the owner can update who has access. This actually highlights how weak the overall separation is.
In his conclusion he writes:
Information is "secure" when a system correctly enforces the access rights currently in the matrix. Information is "private" only when the owner of the information has control over changing the rights in the matrix for the owner’s information.
Professor Mark R. Heckman
Professor Mark R. HeckmanWhat?
Who has ever heard of an information security policy that says the Information Owner cannot define who has access to their own data?
Seriously? That’s what he’s using as a distinction?
So if you’re an InfoSec professional protecting some data, and the Data Owner says that the business or the customer is asking for some authorized party to have access—and it’s all legitimate—do we really think the answer is going to be no?
What reality is this?
Evidently a reality where there’s some kind of artificial boundary that says Security is enforcement of data security policy, while Privacy is the updating of the policy.
People. Please. Stop with this.
Information/Data Security is the art and science of making sure only the right people can access sensitive data. The extremely natural and obvious prerequisite to that is making sure the right policies—as defined by the data owner—are on that data. And yes, and that means keeping them updated.
Stop drawing such sharp lines when they’re not needed in the real world.
Let’s focus all this Pedantic-Chi Energy on finding, classifying, and protecting the data in the first place. That’s what companies actually need help with.