IoT + SSRF: A New Attack Vector?
I think we’re going to start seeing a new type of vulnerability in the next 1-3 years that results from the combination of IoT proliferation and Server Side Request Forgery.
IoT will introduce billions of internet-facing devices, and Server Side Request Forgery (SSRF) will allow internet-based attackers to extract sensitive information from networks abstracted by IoT systems.
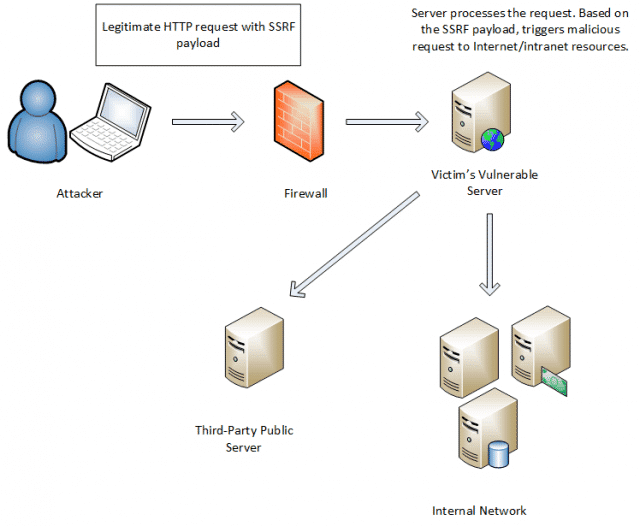
The way SSRF works is through a multi-step process:
You send a crafted request to a vulnerable internet-based system that has an SSRF vulnerability, Target A
That request has within it a second request, which is destined for a Target B on a network that only Target A (and not you) can access
Target A then sends your nested request to the Target B
Target B responds back to you, either through Target A’s response, or directly, depending on the specific vulnerability
The result is that an attacker can potentially extract sensitive data from an internal network or system that it otherwise wouldn’t even be able to interact with.
SSRF requires that you know what Target B is, and what kind of technology it runs, what kind of vulnerabilities it has, etc.
An example might be some sort of sensitive information disclosure, say of the /etc/password file, if you send a specifically crafted GET request to Target B.
But the more Target B’s there are out there in the wild the better (for the attacker). And it’s the same for vulnerable IoT devices that face the internet.
So it comes down to vulnerable combinations. If you combine Target A (IoT system), with Target B (vulnerable application), then you can extract some kind of information from—or even issue some sort of command to—Target B.
It just becomes a numbers game.
If Target A IoT device is deployed in billions of places, and Target B application is as well, then there will be some subset where both are installed together, and that becomes the surface area.
Expect this type of multi-product pivoting to become common as deployments of both IoT systems and various internal tech stacks reach significant numbers.
Notes
Note that this requires both Target A and Target B to have vulnerabilities. Target A in how it passes malicious requests on to internal hosts, and Target B in how it responds to malicious requests.
Image from McAfee.