How to Check for TLS Vulnerabilities Using Nmap

As you probably know, there’s a new encryption vulnerability called Logjam >, which affects the Diffie-Hellman key exchange process.
There are number of online tools that can help you check for it, but it’s often not a good idea to ask random people to see if you’re vulnerable to something. They could be making a naughty Christmas list for all you know.
That’s where nmap comes in. With it’s NSE capabilities > it can check for all sorts of vulns that you’d otherwise have to use one of those sites or roll your own code for:
nmap --script ssl-enum-ciphers -p 443 vulnerable.com
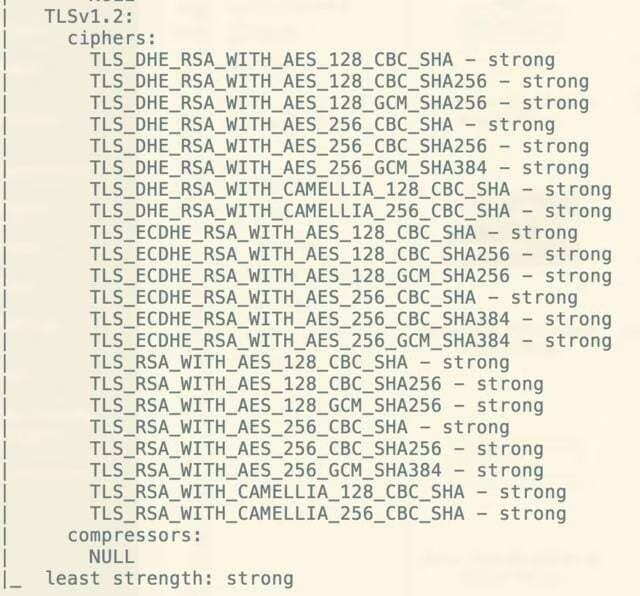
You can also pipe that to grep weak if you want to see just the weak ciphers:

Or you can pipe to grep DHE_EXPORT to see if you support the Diffie-Hellman Export algorithm that’s causing all the commotion.
Either way, you may want to keep this nmap-based TLS check handy since we seem to be conducing this excercise on a regular basis.