Capturing Out-of-band Interactions During Web Assessments
If you’ve not been paying attention you could have missed that web security assessments have recently been massively upgraded.
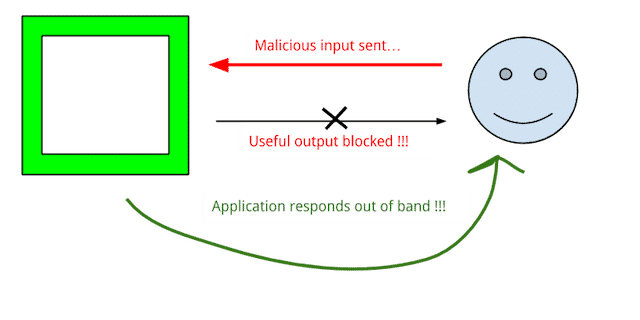
The upgrade came in the form of capturing vulnerability evidence from not just the web application’s detectable output, but from out-of-band indicators as well.
It’s getting harder to get evidence of a successful attack to come back in the output of a page (that’s a good thing), but there are other ways to make an app talk to you—namely having the backend reach out to something you control on the internet.
The more advanced testers have been doing this for years, but it’s been a manual process. For each type of attack you’re sending, you had to configure some kind of listener and leave it running.
But now tools are helping with this process.
Burp Collaborator > and Sleepy Puppy > are two tools for handling this in a more robust way, and if you’re not using them in your web testing (or something similar), you’re almost guaranteed to be missing vulns.
If you’re an independent tester, a testing shop, or anything in-between, you should incorporate this relatively new aspect of web app testing into your workflow.