Building Your Own Dedicated IPSEC VPN in Less Than 10 Minutes
There are tons of VPN options out there, and the field is confusing enough that I did a post on the topic > a while back to help people pick one of the better ones and avoid the scams.
But if you look at the considerations for making a good choice, they mostly reduce to the following:
Privacy
Log retention
Bandwidth
Legal issues
Customer service
Etc.
Just build your own
I sidestep most of these issues by just making my own VPN using one of my favorite projects by hwdsl2 >, called setup-ipsec-vpn. This way you don’t have to worry about your VPN provider messing with your log data, or capturing your packets, or getting served a warrant by law enforcement for something someone else did, or any of that.
VPN services are nice, but my preference is to just run my own VPN from a system I fully control.
It’s just you, a dedicated Linux box that you control, and a full-featured IPSEC VPN all for your own use! Here’s the entire process in just three (3) steps.
It also works on Windows, but…yuck.
1. Create yourself a clean Linux system

You just need a barebones Ubuntu, Debian, or CentOS server. Don’t forget to update the OS and packages.
2. Install the VPN
wget https://git.io/vpnsetup -O vpnsetup.sh && sudo sh vpnsetup.sh
This runs for a couple of minutes and then shows you the credentials to put into your client.
3. Configure your client
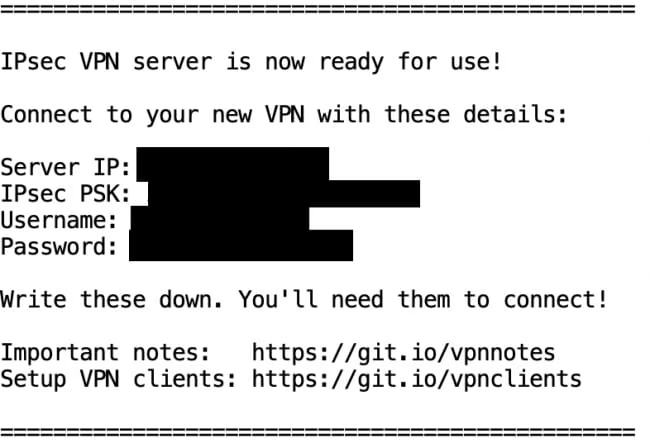
You can put these credentials in basically any solid IPSEC VPN client, including the native ones in macOS and iOS.
Summary
You should be able to run this entire service for the cost of a cheap VPS, which is $5 or $10 a month.
That’s it!
Build a box.
Run a single command to install the VPN.
Plug the credentials into your client.
Connect and enjoy!
Notes
For a middle ground between doing your own like this and using a mainstream service, you can use Zipline, which is a smaller service run by my friend Dan Tentler >.
In the readme there are additional options for providing your own credentials in various ways, so you don’t have to accept and use the ones spit out by the wizard.
You might wonder if this is secure, since you’re running someone else’s script to build the VPN. One, I took a cursory look and didn’t find anything suspect, so that satisfied me decently well. But second, the project is so large and popular that it’s likely received significant scrutiny at this point. There is still risk there, for sure, but I don’t think it’s anywhere near as much risk as using these massively centralized VPN services that are no-doubt being used by criminal elements—and are thus likely to be under tremendous scrutiny.
Dont’t forget to keep both your host and your VPN updated, and make sure you don’t have any services other than SSH (ideally on a non-standar port) enabled, preferably with either a great passphrase or even better key-based authentication with passwords disabled. When we avoid the risk of third-party services we take on the (small) burden of administration. I’m happy with that exchange in this case.