Analysis of Verizon’s 2016 Data Breach Digest
I’m staring to make it a habit to do a quick read and summary of data breach reports.
Here’s the summary for Verizon’s 2016 Data Breach Digest >.
Observations
Covers 2015
Over 500 cybersecurity incidents
Over 40 countries
Over 70 contributors
VERIS is the Vocabulary for Event Recording and Incident Sharing
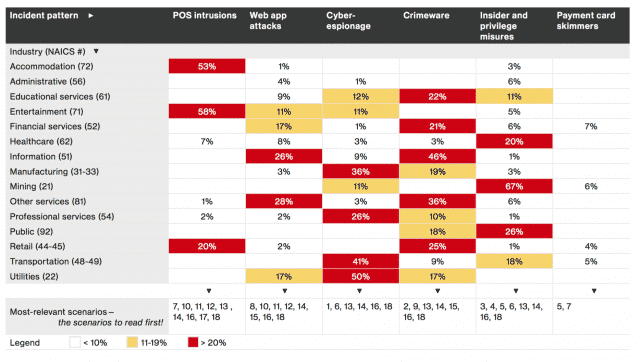
The DBD looks at a subset, in this case 18 scenarios, based on prevalence and lethality
Certain details are modified to protect anonymity
The most common types of attacks in the past have been: POS intrusions, web app attacks, state-affiliated targeted attacks, crimeware, insider and privilege misuse, payment card skimmers, mistakes that compromise security, physical loss, and DoS
They’re focusing on the first six
Witness social tactics being used in about 20% of confirmed data breaches
As one would expect, email is the primary means of communication to the target (72%) followed by in-person deception (18%) and phone calls (12%), with a small amount of overlap across the three means of communication
Having net flow and other such data is invaluable for determining what actually happened
Scenario 1: Chinese company targets head design engineer and infects his system with malware, pivots, and extracts tons of sensitive IP from the network
Scenario 2: Someone clicks an infected link in the office that authorizes bank transfers. They get infected, and now a bunch of transfers are attempted
Scenario 3: Iterator-based web vuln allowed extraction of customer data, which lead to an extortion attempt. They went public to release the pressure of disclosure
Scenario 4: Insider reads CEO emails through misconfigured SPAM filter
Scenario 5: Partner access is abused to extract credit card data
Scenario 6: USB malware infects film studio executive with intent of stealing unreleased video, security catches it, sort of
Scenario 7: Altered PEDs (keypad where you buy things at stores)
Scenario 8: AS400-based SCADA system and numerous internet-facing vulnerabilities lead to PII theft and the ability to modify chemicals going into water
Scenario 9: infected system on BYoD network blacklists corporate network because they shared the same NAT egress point
Scenario 10: banking victim has malware infect and decrypt encrypted ATM transactions due to high volume of data to start from
Scenario 11: SQLi issue on payroll site let attackers modify and then fix paycheck values and destinations to avoid detection
Scenario 12: Attackers compromise custom CMS upload function to extract data about what material will be on what boats at what time. They then actually pirate the ships in question
Scenario 13: malware in R&D department looking to extract key research
Scenario 14: data extraction over DNS
Scenario 15: ransomware
Scenario 16: advanced malware creates P2P mesh network using UDP port 53 as the daemon
Scenario 17: RAM-scraping POS malware
Scenario 18: SQLi, password dumping malware, notification by the FBI that their systems were being used
Summary
These types of reports are fascinating.
Sure, there is usually some marketing of services. And it isn’t science where you’re getting perfect samples of the real world in a balanced way. But you are at least hearing about real incidents in the real world.
Definitely go read the whole thing >.
Notes
Verizon’s Business Group was recently breached themselves, so a lot of this data has been leaked. It can happen to anyone.