AI's Morose Mania
The more excited we are as developers, the more we have to worry about knowledge workers


TOPIC: In this episode, Daniel takes a look at the 2020 Verizon Data Breach Investigations Report. He looks at the key findings and talks about what they might mean to us going forward.
The newsletter serves as the show notes for the podcast.

The Dataviz Game on Point
Verizon’s Breach Report is one of the best infosec reports out there, and I’m always excited when I hear it’s been released. This year—with the lockdown—that’s even more the case. So I decided to do a dedicated edition of show for it.
I have to say, the report started strong with the very first thing I see being a super clean data visualization like we see above.
You can download the full report here.
So let’s get into it.
There’s lots of religion around definitions (trust me, I have my own church), so it’s important to lock that down in the beginning. These are the three that I see the most disagreement on when people talk about this report.
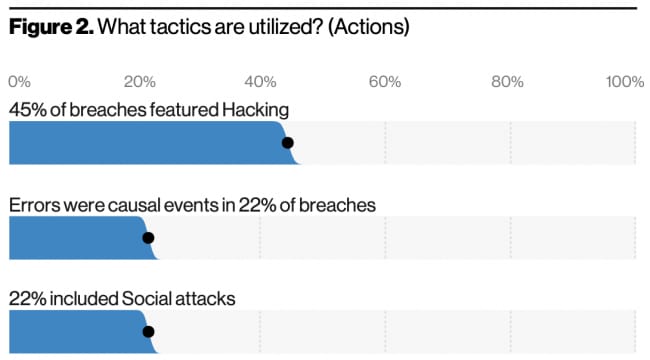
Top tactics utilized
This year, they looked at 3,950 breaches and 157,525 incidents—32,002 of which qualified to be analyzed by them
45% of breaches involved Hacking
Errors were causal events in 22% of breaches
72% involved large business victims
58% had personal data compromised
70% were perpetrated by external actors (30% involved insiders)
Organized crime was behind 55% of breaches
86% were financially motivated
Web Apps were involved in 43%
37% stole or used credentials
22% involved phishing
Phishing is usually going after credentials, but stealing money is continues to rise in popularity
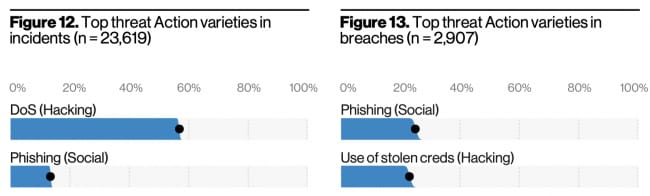
Top actions for incidents vs. breaches
They say external actors have always been the majority, and that the rise of internal breaches is from better reporting, not increased frequency
The top actor was by far Organized Crime, at 55%
Nation-state, end-user, and system admins each took around 10% of the actor pool
The Error incident type continues to increase, with most other types falling
Hacking, social, and malware have fallen the most
The top 2 incident threat actions were DoS, and Phishing
The top 2 breach threat actions were Phishing and Use of Stolen Creds
Errors are now as common as social attacks, and more common than malware attacks
The top malware type is Password Dumper, because it really is about getting those creds
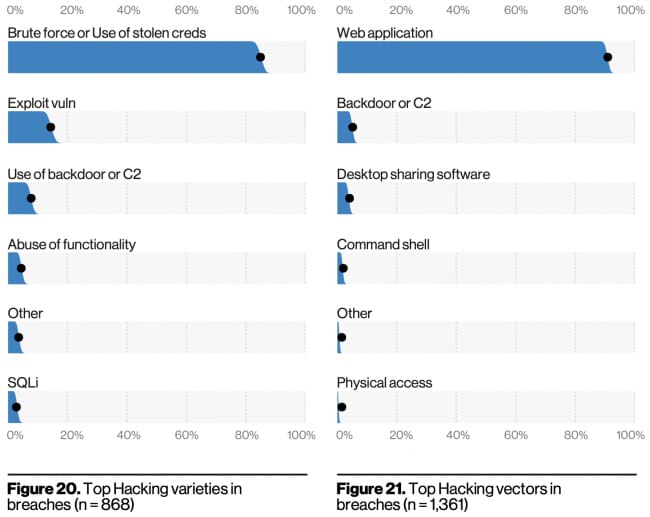
Hacking types and vectors
The top three ways of getting the malware are email link, direct install, and download by other malware
Within hacking, web applications accounted for over 95% of breaches
Over 80% involved using brute force or stolen creds
There was relatively little vuln exploitation or use of backdoors/C2
Social actions arrived via email over 96% of the time
Breaches that take days or less are rising, while those taking months or more are declining
They’re showing cyber-espionage as being down, which is surprising to me
DDoS is way up, both in numbers of attacks and the weight of them
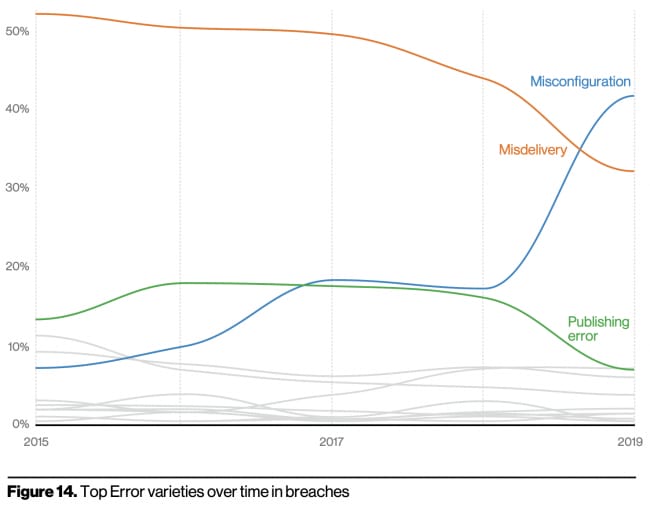
Misconfiguration is becoming a huge issue
I find it really interesting that in the top threat actions for breaches—so, successful incidents—the top 5 included: phishing, stolen creds, misdelivery (error), and misconfiguration (error).
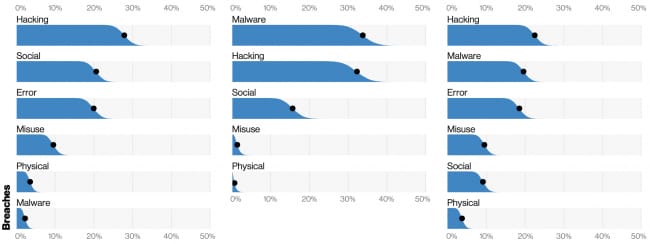
Different techniques used in different phases of the attack
On page 101 they mention that they’re standardizing their recommended controls on the CIS 20, which I think is smart.
So it seems like the major themes are:
Phishing (which is usually used to steal credentials)
Email security (because phishing)
Web applications (which are used to extract and input stolen credentials)
Stolen Creds (which are usually used against web apps)
In short, credentials.
And the second big theme seems to be misconfiguration, which I’ve always been on about, and is also why I’m so obsessed with recon.
All summed, this is another phenomenal report by the team at Verizon. I think I liked the structure and visuals of this report more than any other so far, so happy to see them constantly innovating on how they present their data.
Get a weekly breakdown of what's happening in security and tech—and why it matters.
Tons of data is useless if you can’t find compelling ways to display it, and I commend them for their work in that regard.
Remember, what you see above is just some highlights that jumped at me, but different readers will notice different things. So I definitely recommend you read the report yourself.
See you next year for the 2021 version.