5 Things You Didn’t Know You Could do with Nmap
For those who have been in information security for a while, nmap is like a warm and familiar blanket. Except this blanket kicks ass. It is—without question—the most versatile portscanner ever.
A lot of people know that.
Read my masscan tutorial >.
What fewer people know, however, is that with NSE scripting functionality > nmap can do things you wouldn’t expect from a portscanner. There are faster scanners >, but there’s nothing as versatile and indespensable.
Let’s look at 10 things you can do with Nmap that might surprise you.
Nmap NSE
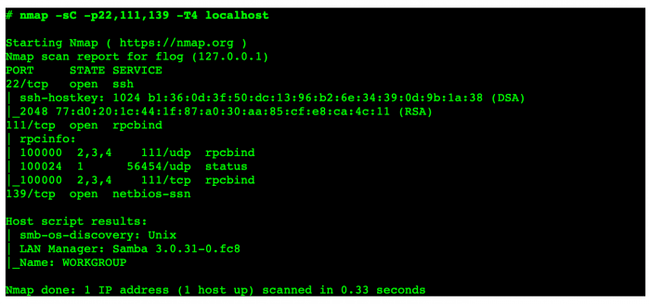
Typical NSE Output
First, what are NSE scripts?
NSE stands for Nmap Scripting Engine, and they basically allow you (yes, you) to write and share additional functionality that can be bolted onto the scanner we all love.
NSE somewhat blurs the line between portscanner and vulnerability scanner.
So in addition to checking for open ports, learning more about the service running on it, etc.—you can also further interact with it, e.g., see if it’s configured correctly, see what information is available, see if it’s using weak credentials, etc.
It basically turns Nmap into a platform for interacting with network services.
Nmap NSE Examples
There are currently 598 NSE scripts, which you can find under the scripts directory in your nmap path.
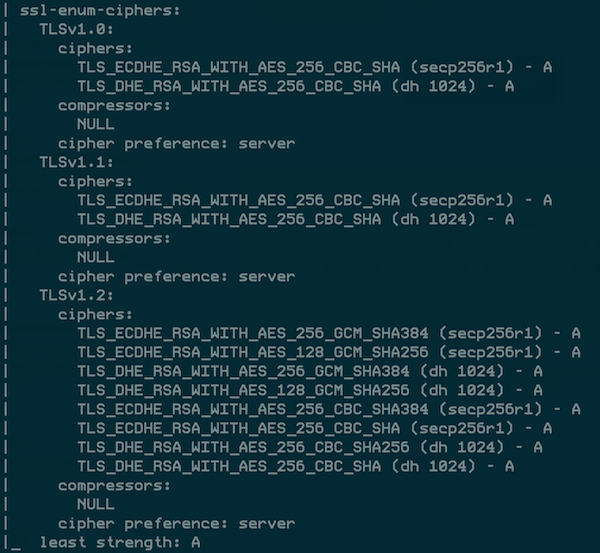
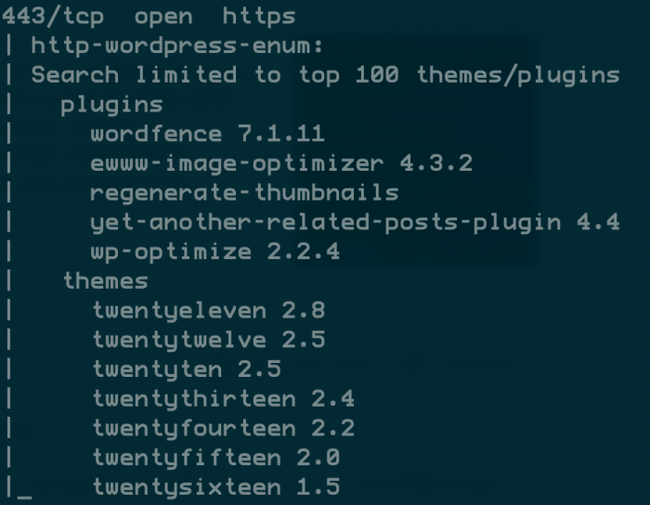
Each of these has better standalone alternatives, but sometimes it’s better to get good enough data from a common tool like Nmap.
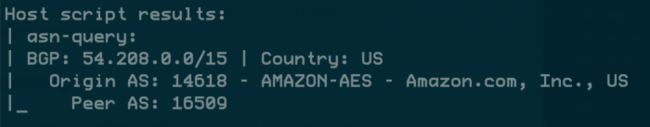
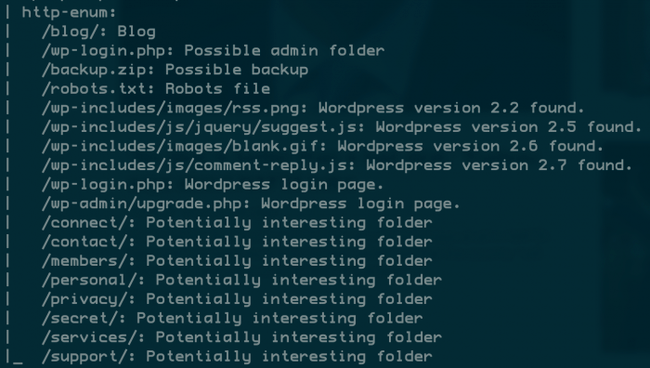
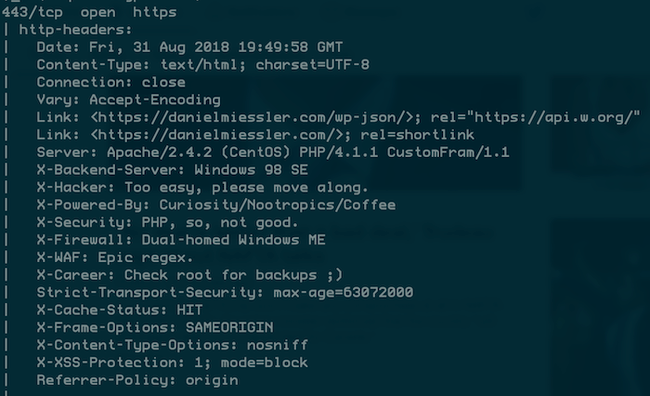
More scripts
There are tons of scripts for tons of common protocols.
SMB
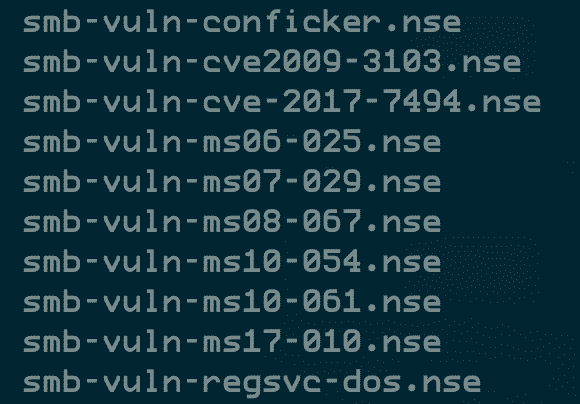
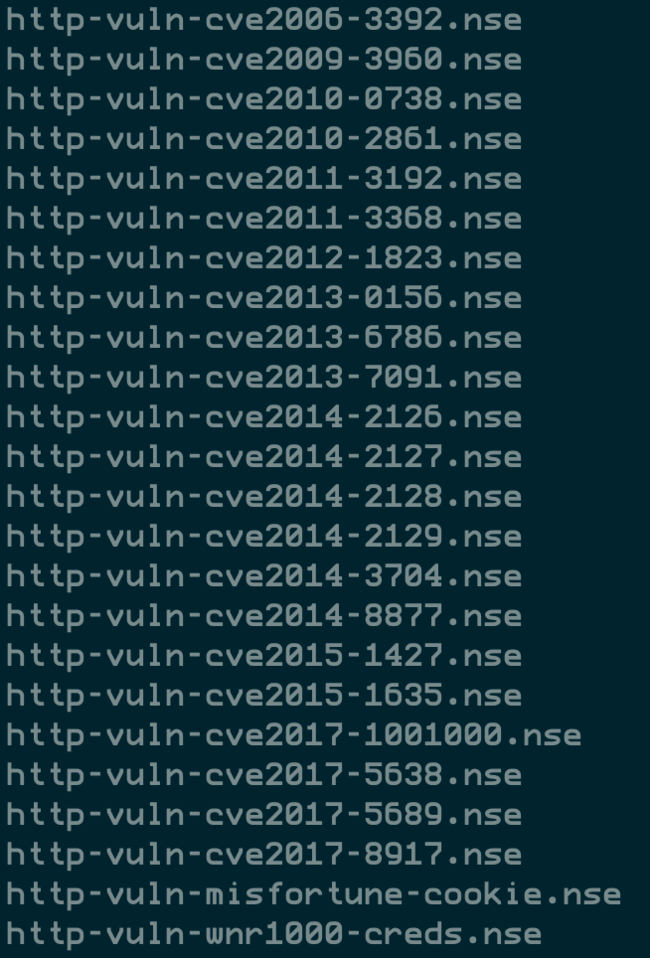
HTTP
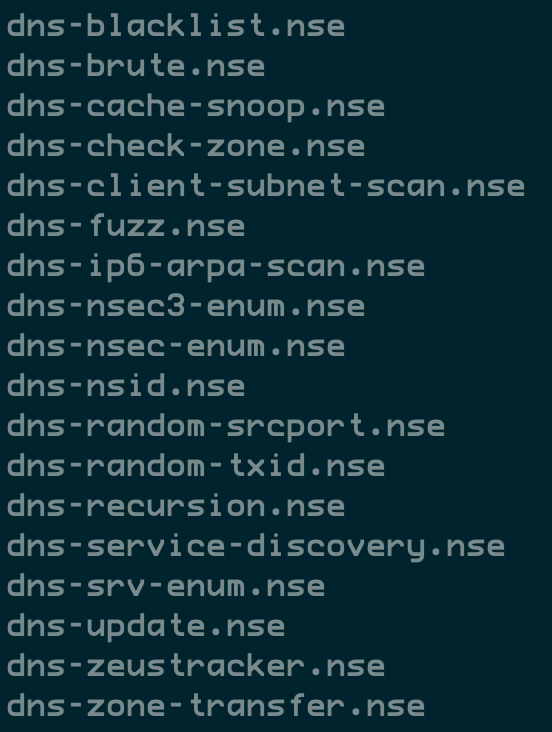
DNS
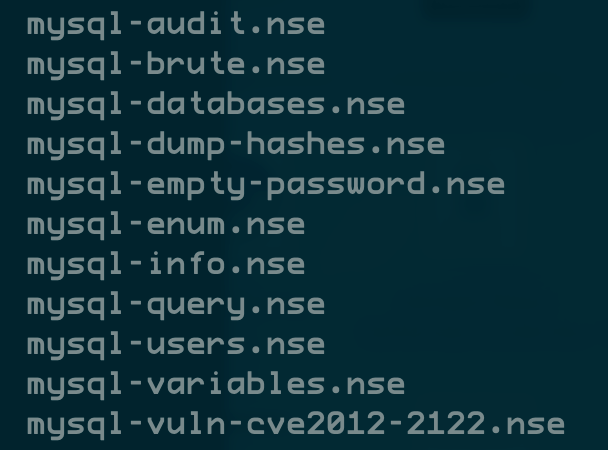
MYSQL
Summary
Nmap may not be the fastest portscanner, but it’s the most versatile.
With its NSE functionality, the lines are blurred between portscanner and vuln scanner.
The next time you have something common you want to do with a service, check to see if there’s an NSE script available. Let Nmap do the work for you.