The VIA Model of Security Filtering Technologies
I inwardly smile when I hear the term "Unified Threat Management". It means different things to different people, but to me it means consolidating the different "types" of security filtering, e.g.:
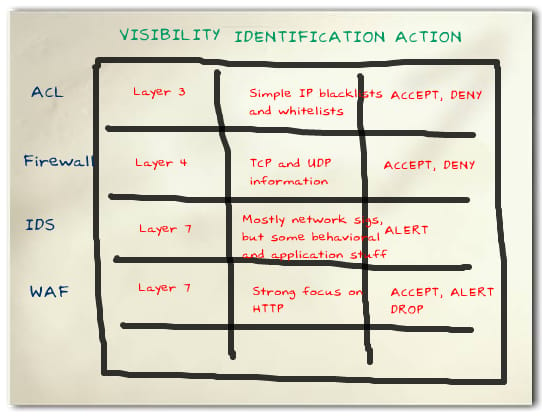
ACLs
Firewalling
Stateful Inspection
Deep Packet Inspection (whatever that is)
Network Intrusion Detection
Network Intrusion Prevention
Application Security Filtering (Web, Database, etc.)
…onto a single device.
This isn’t really all that special. The only reason things didn’t start out this way in the first place is because the technology wasn’t there yet. We didn’t have the horsepower on the devices nor the various types of inspection to leverage.
So now the technology is finally catching up, and the marketing folks evidently decided not to go with, "UTM: The Way Things Were Supposed to Be Originally!" as their slogan.
The VIA Model
The reason combining these various pieces is brutally obvious is because they’re all doing the same thing. There is, fundamentally, very little difference between a router ACL and a Web Application Firewall. Once distilled there are basically three components to any security filter:
Visibility: what portion of the input does the system inspect?
Identification: what types of knowledge and/or intelligence can be used evaluate on?
Action: what can be done once something is found?
So what’s the difference between an IDS and an IPS? In the action phase you get an extra option to drop. Awesome. What’s the difference between an IPS and a WAF? WAFs understand HTTP better (the identification phase); they both see through layer 7 and can drop stuff they don’t like. Looking at it this way, even a router ACL and a WAF aren’t that far apart; the WAF simply beats it in all three VIA categories.
So no matter how cool the name of your filtering system is, it’s only doing a combination of those three things. It could be "Deep Packet Inspection", or it could be, "Bob’s Packet Looker Thingy"–either way you have to a) see packets, b) find stuff in them, and c) do something when you do.
That’s why the future of security filtering is for every trust boundary and every endpoint to be running all of these simultaneously. You see the traffic once, run it through all your various identification pieces, and then you take whatever actions based on your policy.
The fact that we’re getting to that point doesn’t constitute evolution; it just means we’re finally getting to where we should have been all along. ::
Hat tip to Markus Ranum for pointing me in this direction back in 2003 with a talk on the difference (or lack thereof) between IDS and IPS.