The Subsequent Waves of log4j Vulnerabilities Aren’t as Bad as People Think
If you’re reading this you’re underslept and over-caffeinated due to log4j. Thank you for your service.
I have some good news.
I know a super-smart guy named d0nut > who figured something out like 3 days ago that very few people know.
Once you have 2.15 applied—or the CLI implementation to disable lookups—you actually need a non-default log4j2.properties configuration to still be vulnerable!
Read that again.
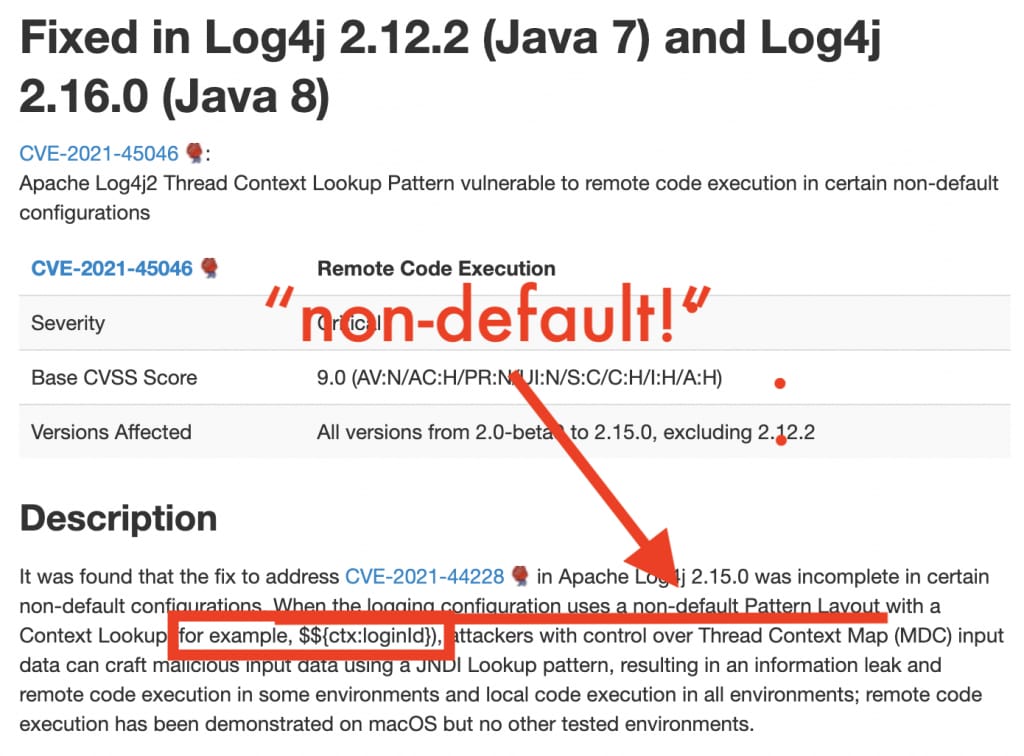
The bypasses of 2.15 and the NoLookups CLI change don’t affect people unless they have non-default logging configurations. From the Apache advisory:
It was found that the fix to address CVE-2021-44228 in Apache Log4j 2.15.0 was incomplete in certain non-default configurations. When the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example, $${ctx:loginId}), attackers with control over Thread Context Map (MDC) input data can craft malicious input data using a JNDI Lookup pattern.
Apache Project Security Advisory >
Apache Project Security Advisory >"Certain non-default configurations". I’ve never heard a sweeter set of syllables.
These can also be set in log4j2.xml or programatically.
So you need to have changed your configs to include patterns like:
${ctx:loginId}
${ctx
${event
${env
…etc to be vulnerable to a 2.15 patch level or a log4j2.formatMsgNoLookups or LOG4J_FORMAT_MSG_NO_LOOKUPS = true bypass!
That’s huge! And Nate figured this out like 4 days ago!
He mentioned to me multiple times this wasn’t as bad as people thought, but he wasn’t shouting from the rooftops so I didn’t listen well enough. Shame on me.
He also happens to have a strong meme game.
Summary
The first vuln was just as bad as everyone thinks it is. Or worse. It did not require this non-default logging configuration.
But if you are patched to 2.15, or mitigated with the NoLookup config, you are no longer vulnerable unless you ALSO have a logging config option set in your log4j2.properties file that re-enables them.
So, if you’re already patched to 2.15 and/or have the mitigation in place, and don’t have non-standard configs—which you should confirm—you might be able to sleep for a bit.
And of course of course—keep in mind that this all only pertains to vulnerabilities we know about today. And the internet moves fast.
Finally, d0nut > is awesome and you should follow his work.
Notes
This also applies to the DoS that 2.17 addresses.
Thanks to Nate for the great find!