Cyber Pearl Harbor Is Happening Right Now — It’s Ransomware

Since 2007 the InfoSec industry has been talking about TheBigOne™—the event that would change cyber threats from annoyances to existential concerns.
They called it Cyber Pearl Harbor.
This doesn’t mean it can’t still happen.
The idea was that it’d be some massive blast that would take out the country’s power grid, or disable the entire internet, along with what they used to call e-commerce. That moment hasn’t happened (yet), but I think we’ve become the frog in the boiling cyber-water.
Ransomware is the Cyber Pearl Harbor we’ve been waiting for all along. It just looks different. Rather than being the one big blast, it’s more of a steady bombardment.
Some stats:
At the time of this writing, Google News returns 7,460,000 results for the term Ransomware. More >
SafetyDetectives reports the average cost of a ransomware-caused downtime incident has risen from $46,800 in 2018, to $141,000 in 2019, to $283,800 in 2020. More >
The UHS hospital network, which is a Fortune 500 company with over 400 hospitals, has had multiple hospitals affected which required them to redirect patients to other options. More >
According to Datto, Ransomware attacks are costing businesses more than $75 billion a year. More >
Ransomware groups simply evolve too fast for small school districts with no IT staff.
She tried to reroute to another hospital and didn’t make it.
A woman recently died in Germany after she couldn’t receive critical care at her local hospital due to an attack. More >
A ransomware attack against the New Orleans city government in early 2020 cost the city over $7 million dollars. More >
New York City’s capital was hit with a ransomware attack in 2019 that took several key services offline. More >
IBM says 1 in 4 of attacks its X-Force Team sees is caused by Ransomware. More >
Ransom demands are increasing exponentially. In some cases, IBM Security X-Force is seeing ransom demands of more than $40 million. More >
The skill and preparation asymmetry between attacker and defender is drastic.
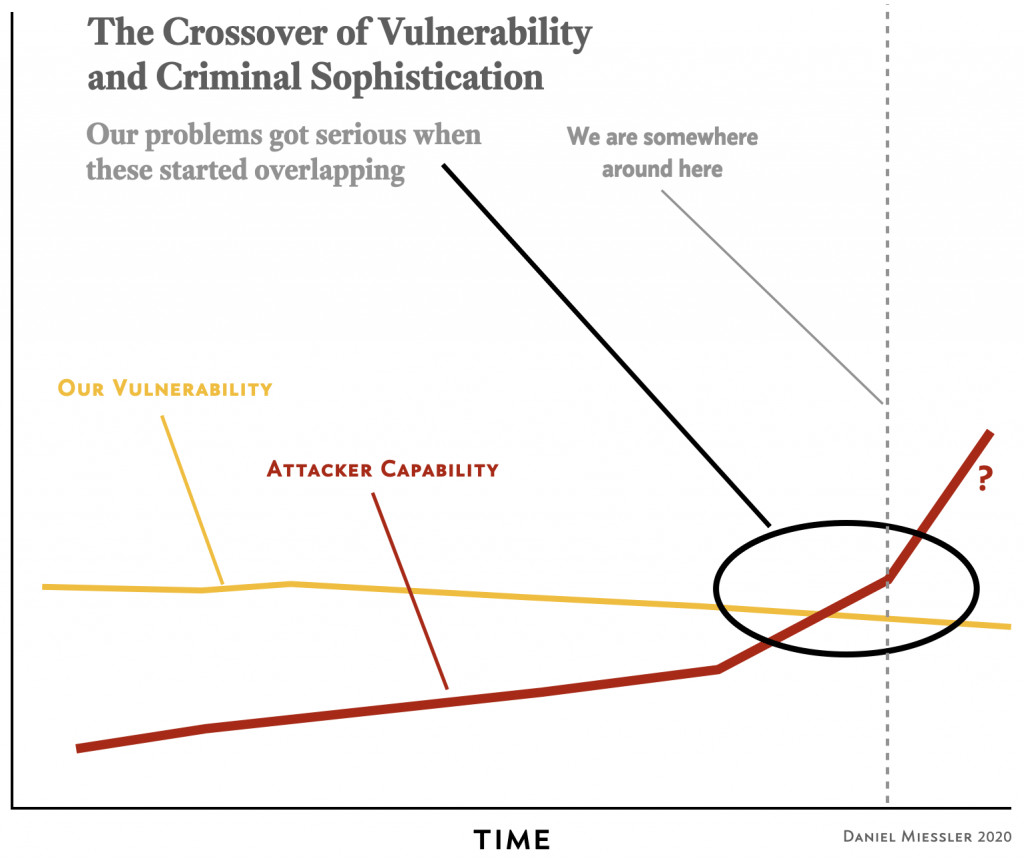
My rough scribble of how ransomware sophistication surpassed our defensive capabilities somewhere around 2018
I think the only reason we survived this long without serious disruption to business—like we’re seeing now—is because attackers didn’t have their acts together. Their tooling wasn’t nearly as good as it is now, and they hadn’t linked their tooling with the business models.
Today there are multiple routes to make money from an insecure business. Once they get in—via RDP or Phishing or Drive-bys >—they are not only extorting people who want to get their data back.
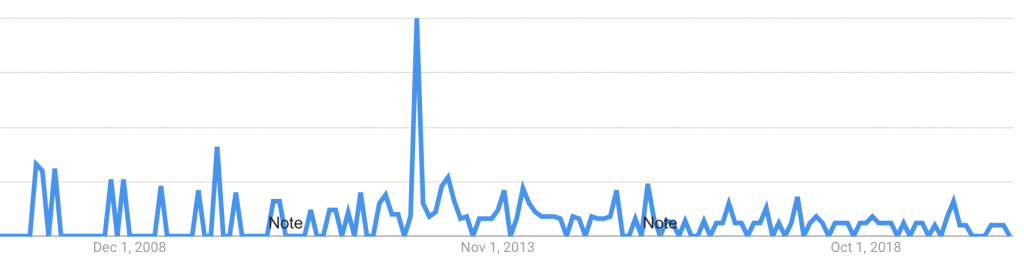
Google Trends Data for the term Cyber Peal Harbor
As a security person I sometimes have to admire their creativity.
Many groups have come to realize that some companies have good backups, so they start by stealing a copy of the data for themselves at the beginning of the attack. Then if someone doesn’t want to pay they can threaten to release the data and create a public incident.
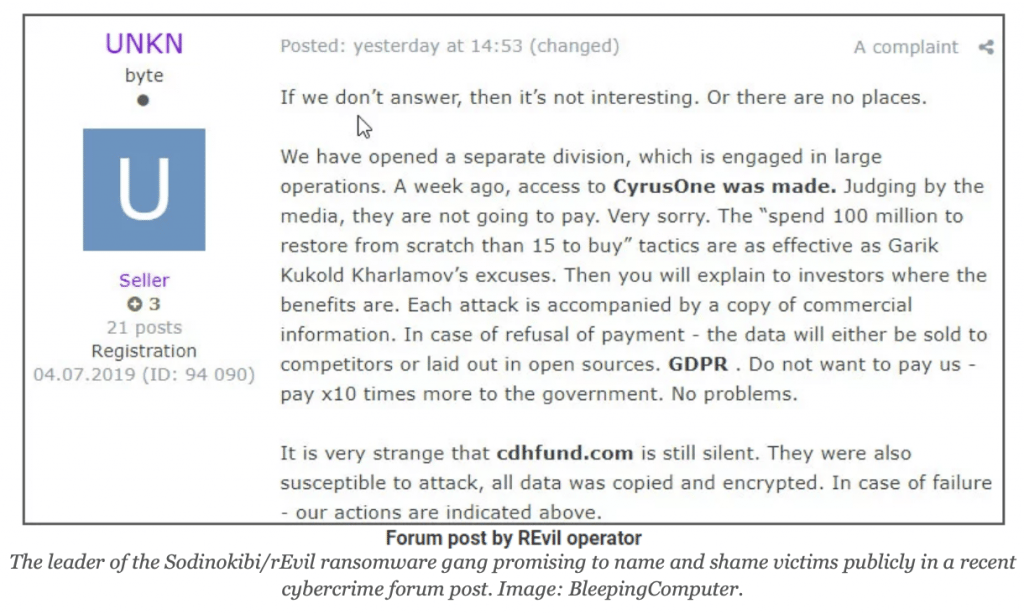
A threat to release data. Image from BrianKrebs.com.
These attacks don’t seem to be slowing down, and the attackers keep getting better at them. They’re improving their tools, they’re improving their business models, and they’re constantly evolving their techniques for getting companies to pay using social engineering.
The question is—how fast are our schools and hospitals and local governments improving our defenses to stay ahead of the attackers on all these fronts?
Nowhere near fast enough. That’s my answer.
Even medium and large businesses struggle to handle this threat, and that’s with dedicated security staff to help them. The small businesses, government orgs, and other entities that lack security talent and budgets are hopelessly outgunned.
If enterprises that spend millions on cybersecurity struggle with this, what hope is there for local governments?
I think the attackers are just now hitting their stride. I think they’re going to get more deadly, more efficient, and smarter about who to target at what times.
Schools have had to shut down over this. Hospitals. City governments and businesses. And as far as I can tell there’s no end in view here. We don’t have enough security people > to cover the surface area, even if these targets had the budget to hire them.
We can stop waiting for Cyber Pearl Harbor. It’s here already, and we’re living it.
Notes
I think what’s going to happen before too long is the federal government will tap the endpoint vendors on the should and say: "Hey, the country needs you. Here’s several hundred million dollars: you now need to get Crowdstrike, Sentinel One, etc., installed on every school and government computer in the country. Go."
I’d put BEC in the same conversation, but not the same sentence.