The Connected Web: Why It’s Time For Strong Authentication

It’s getting exciting in the world of cross-network authentication. Let’s review. I can now:
sign into Facebook automatically using OpenID > (with two-factor authentication >) or Google
sign into FriendFeed > using Google, Twitter, or Facebook

We’re quickly approaching the point where we’re going to be able to log into one major service (Google, Facebook, OpenID, etc,) and from there access all of our other services without authenticating.
As it stands now, I can already log into my OpenID provider, visit the Facebook homepage, and be transparently logged in. Today this works on Facebook. Soon something like it will work for your bank as well.
This is a good thing, but there’s a catch.
Security
While this is completely phenomenal from a functionality standpoint, we need to consider the fact that single-sign-on (SSO) raises a serious security concern: it significantly increases the impact of an account compromise.
If my OpenID account gets me into Facebook, and my Facebook gets me into Digg and DISQUS and FriendFeed (where I can post to Twitter, of course)…then a compromise of my OpenID account means a compromise of all those other accounts as well. Basically, once someone gets into your main service, your entire online identity can be hijacked.
Authentication Strength: More Important Than Ever
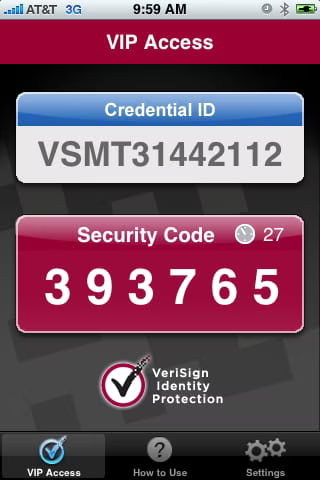
As single-sign-on solutions get more popular (i.e. now) we are going to have to give significantly more attention to our authentication standards and processes. Traditionally this has meant having a strong password, and while that is an essential piece of it, it’s arguably no longer enough.
What we really need to do is move to a strong/multi-factor authentication system. This means combining at least two of:
something you know (passwords, pins)
something you have (tokens, smartcards)
something you are (biometrics)
So if someone guesses your password to my OpenID account, for example, they still can’t get into my account. They know my password, but they don’t have my mobile phone with my soft token on it. That’s multi-factor authentication, and it improves your security greatly when done right.
My current recommended way of doing this is by adding two-factor authentication > to OpenID, which can be done via Verisign PIP > for free. VIP > can be used to add two-factor auth to major sites like eBay > and PayPal > as well, and soft tokens are available for popular mobile phone platforms > if you don’t want to carry an actual token.
Strong Authentication Alternatives
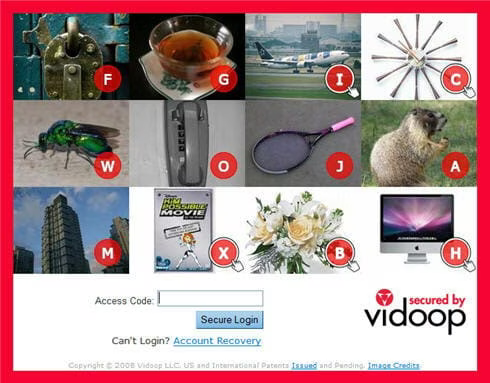
In addition to tokens a number of other innovative options are available for multifactor authentication. Vidoop > is an interesting system that combines OpenID functionality with a unique picture-based authentication system. It’s not technically multi-factor since it relies on something you know twice (password, then the images), but it’s still considered strong authentication.
Plus there are number of systems that use other things we commonly have with us to provide an additional factor of authentication, like sending a one-time password to your mobile phone via text message.
Conclusion
Social web service integration is upon us. Very soon, signing into websites using local credentials is going to be an indication of one of two things: 1) your single-sign-on system is broken, or 2) you’re using a website so ancient that you might want to consider an alternative.
This is progress, and it’s progress we should embrace, but we need to keep the risks in mind and take steps to mitigate them. So yes, enjoy the new powers given to you by single-sign-on, but do your best to protect yourself by looking for strong/two-factor authentication options within your favorite online services. ::
Links
[ Strong Authentication | wikipedia.org > ][ Two-factor Authentication | wikipedia.org > ][ Single Sign On | wikipedia.org > ][ OATH | openauthenticaton.org > ][ Facebook Connect | facebook.com > ]