Security Report Analysis: Forrester Automated Malware Analysis Q2 2016
In this Security Report Analysis (SRA) series I look at various security reports and pull out the main points.
This doesn’t replace a complete and detailed read of these reports, but at least you’ll get exposed to some of the key takeaways that you might not otherwise have seen.
REPORT: The Forrester WaveTM: Automated MalwareAnalysis, Q2 2016
Key points
[ NOTE: These points are a combination of the report’s actual points combined with my own interpretation of them. Some of the analysis is not theirs, in other words. Don’t take this as me putting words in their mouths, but rather me trying to parse and interpret for my and your benefit. ]
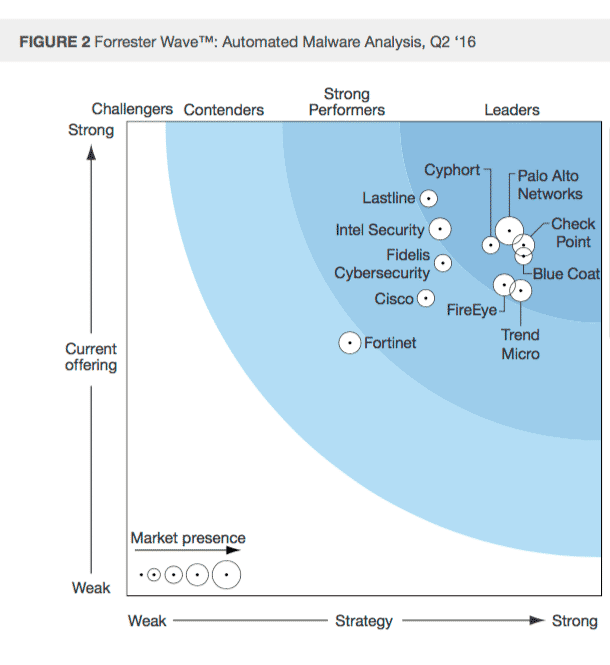
Palo Alto networks, check Point, Blue coat, cyphort, trend Micro, lastline, Fireeye, and intel Security are doing well
Fortinet is lagging
Security professionals really need the automated malware analysis functionality because they don’t have much of another option
[ NOTE: Automated malware analysis seems to be having any technologies looking for malware, which seems a bit broad given that it could include anything from antivirus to nextgen firewalls to whitelisting. ]
AMA (automated malware analysis) finds the most stuff according to the report, which makes sense. What’s the alternative? A team of 20,000 humans inspecting every packet?
Threat intelligence is becoming part of these platforms
Many of the products have 0-day detection and information sharing
Virtualization is different than emulation when it comes to finding new issues
Detection capability is NOT EQUAL to effectiveness in an organization; you have to be able to do something with those results
I wonder why Sophos wasn’t included?
Palo Alto is leading (which I already knew)
Fireye is still kicking ass in the malware analysis space
Fidelis is worth looking at with regards to dynamic analysis and analytics
Analysis
AMA seems like a strange thing to call this space. It’s really just a security platform. What does this type of security technology do? Firewalls, AV, proxies, etc. It does three things:
Looks at stuff
Checks to see if the stuff is bad
Does something if/when it finds it
[ NOTE: HT Ranum circa 2003 ]
Whitelisting is a bit different, and there are some novel approaches out there, but these are the fundamentals.
Platforms that do this in a unified way, across multiple parts of the org (endpoint, server, network, memory, files, applications, etc.) are the ones that are going to win.
Perhaps that’s what they mean by AMA, and if so then I’m ok with that.
Summary
Get a solid security platform like PAN or CheckPoint or something similar
Configure it correctly
Make sure it’s seeing all your traffic (or as much as possible)
It’s not about what you can detect; it’s about what you can do something useful with
This is a great way to add security in an organization, and is far better than adding 20 point solutions that have their own interfaces.
Platforms are the future for everything, and that includes security products.