Ransomware Groups Add a Third Threat Vector: DDoS
I’ve been writing a lot > on ransomware recently >, and wanted to comment on an interesting new development in attackers’ toolchests.
At first they started with:
If you don’t pay, you won’t get your data back.
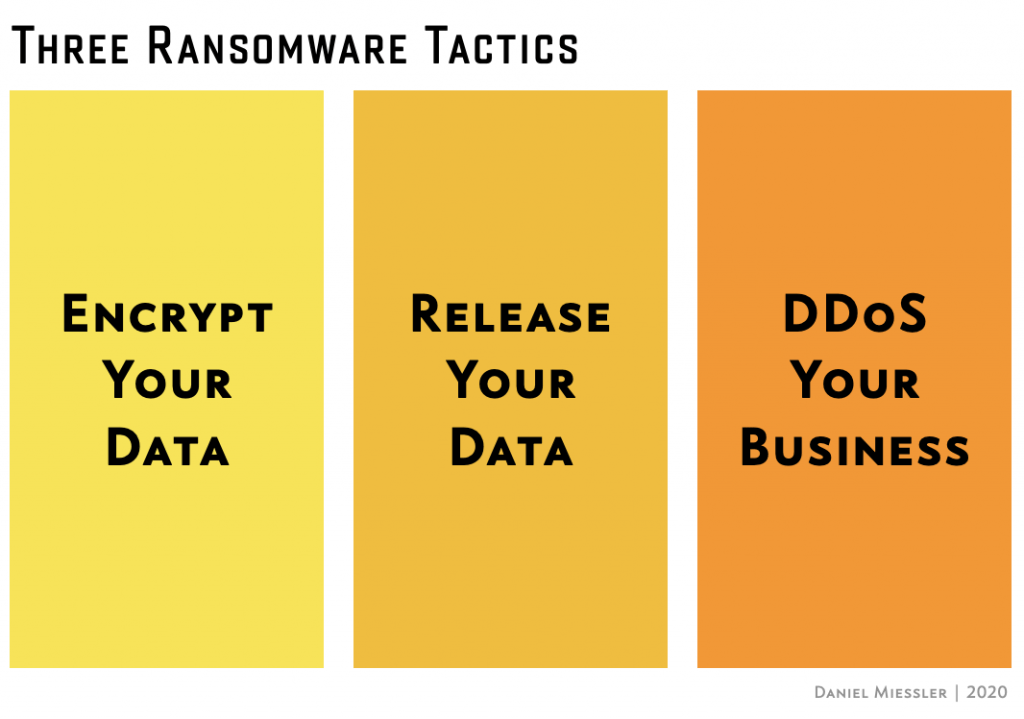
This is the original ransomware tactic. It’s a denial of service against your data. You pay, and you (sometimes) get your data back.
Then, within the last year or two, they started adding a second technique, which is stealing the data before they encrypt it—and then if you don’t pay they threaten to release that data and embarrass your business.
If you don’t pay, we’ll release this data to the public.
And now they’re adding a third tactic, which is a denial of service again, but at the business/network level. They threaten to DDoS your company so customers can’t use your service.
If you don’t pay, we’ll knock your business offline.
This is a brilliant set of options for an attacker, and they seem to be moving from left to right, which is the order in which they became popular. So they start by asking if people want their data back. If they have good backups, or don’t need the data, they threaten to release that data to the public, and if that doesn’t work they now seem to be pivoting to a threat to take the business offline using a DDoS attack.
All three cases target the business’s ability to make money. The first and third are direct hits to the ability to do business itself, and in the case of embarrassment, it’s an attack on reputation, finances, and resources via lost customers, fines, etc.
They also get to point to real-world examples in their threats, such as the situation in Las Vegas where student information was just leaked > because a school declined to pay a ransom.
The thing that makes these groups so dangerous is their ability to evolve their attack techniques. And that’s not just the quality of their malware, but the effectiveness of their approaches to victims.
Some groups play the sympathy card, and apologize for asking for the ransom. Others pretend their threats are "findings" that are part of a bug bounty program, which gives the company the out of paying security researchers instead of hackers.
Whatever the tactic, the problem is that the attackers are evolving a lot faster than defender defenses. And we should expect that gap to continue and even widen in the coming months and years.