Notes and Analysis on the 2017 Verizon DBIR Report
Verizon just released the 10th edition of their Data Breach Investigations Report >, and this is one that I always look forward to. Here are the things that stood out to me, along with some comments on them.
Verizon classifies an Incident as a security event that compromises the integrity, confidentiality or availability of an information asset. It defines a breach as an incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party.
75% of breaches were perpetrated by outsiders.
25% involved internal actors.
I wonder what "involved" means there. Used their access, or there was collusion?
62% featured hacking.
51% included malware.
81% involved stolen or weak passwords.
Not surprising at all. The number is quite high, though.
Around 40% of victims were either financial or healthcare.
66% of malware was installed via email attachment.
This points to phishing as being an extremely powerful vector, which we knew but it’s good to see it reflected here.
Crazy idea: what if people use malware in hacking? Not trying to be snarky, just think we might be able to find better words to make this distinction.
73% of breaches were financially motivated. 21% espionage.
27% discovered by third parties.
21% espionage is interesting. Feels higher than I would have guessed just based on how much cybercrime there is.
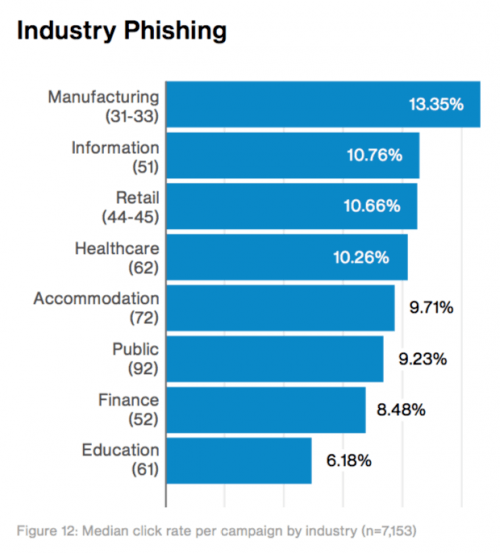
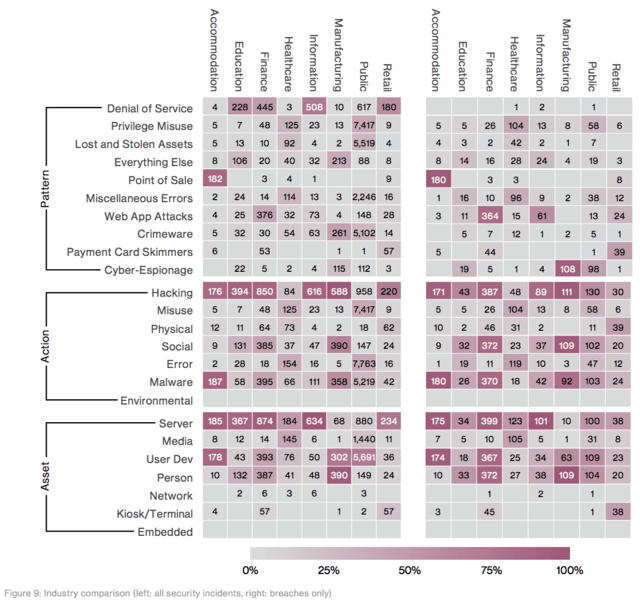
This is some great analysis on median click rates for phishing, by industry. The high numbers for manufacturing doesn’t look good for supply chain security.
Finance and retail look to be the primary targets for DDoS.
Healthcare had a massive number of breaches that came from insider misuse.
Ransomware accounted for 72% of malware incidents in the Healthcare industry.
Cyber-espionage was the top motive for attacks against manufacturing
Espionage is also the top motive in attacks against Public Administration.
The vast majority of breaches in Public Administration were state affiliated (90 out of 113).
Retail’s biggest problems are DDoS and POS compromise.
93% of social incidents were Phishing.
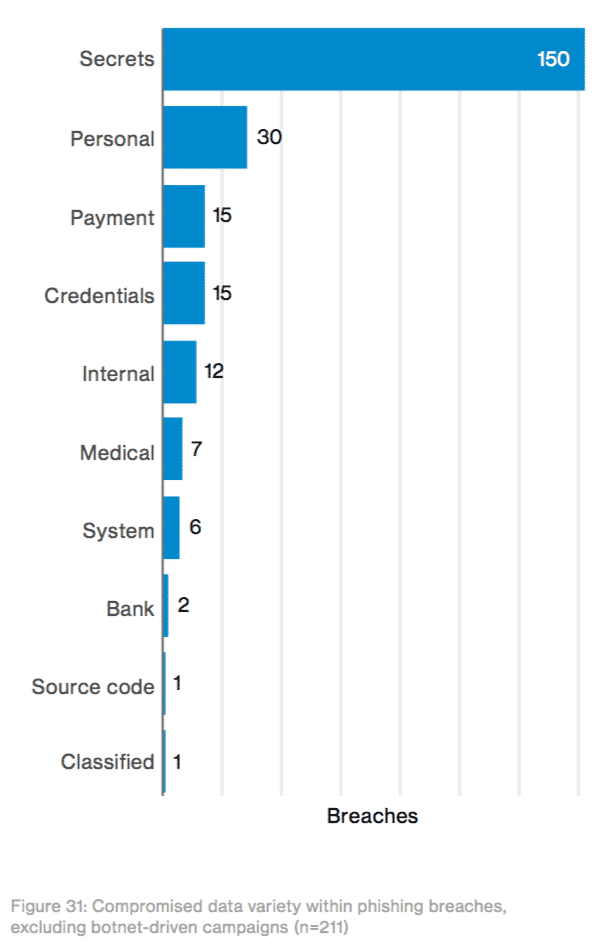
Ransom notes are the most profitable form of writing. ~ 2017 DBIR
Web App Attacks resulted in the most breaches, which is expected since they’re facing the internet the most.
Makes sense, right? Web attacks and phishing—both of the things that external entities can touch you with.
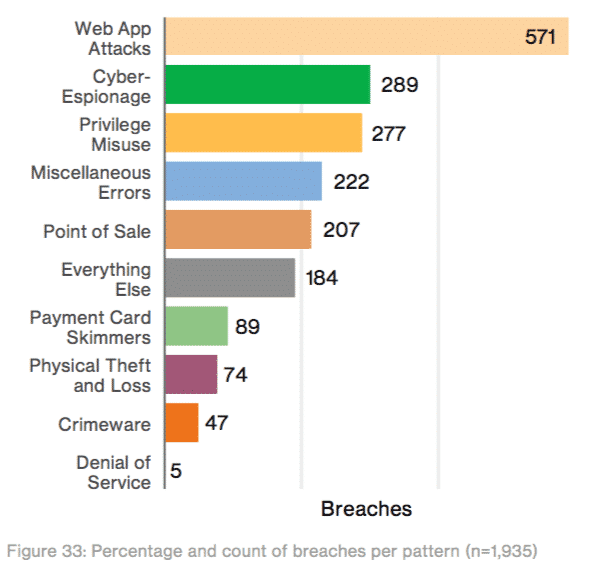
Telephone DDoS is becoming more of an issue, evidently.
Summary & Analysis
Another strong report by Verizon. I especially love the industry breakdowns towards the end of the report.
What I’d really like to see a report on is the reasons for the failures. It’s great to know how broken we are, but why are we broken in this way?
We have budgets. We have security teams. I hardly ever go into a company with over 1,000 people who 1) don’t have have a security team, and 2) aren’t massively focusing on the wrong things. As someone said recently, it’s not that we have a talent shortage (necessarily), but instead that we’re mismanaging the resources that we have.
I know many security teams of 10 or 50 or more who are intensely busy—and who could remain that busy for years—but aren’t getting their company’s risk level anywhere near the acceptable level.
Our priority should be figuring out how that’s possible. What forces inside an organization can keep a large security team simultaneously busy and ineffective?
That’s the enemy we must name and face.