My Takeaways from the 2019 DBIR Report
Many years ago, Verizon started a trend by releasing their Data Breaches Investigations Report, and today there are dozens of companies releasing similar offerings. But even with all the competition—some of which are quite good—the original DBIR report is still my favorite.
Here were my main takeaways from this year’s release.
Meta
This is the 12th year of the report
As usual, it’s built from real-world data
This year they included 41,686 security incidents and 2,013 data breaches
There were 73 data sources spanning 86 countries
Perpetrators
69% of attacks came from outsiders
34% involved internal actors
They say only 5% involved partners, which I would thought would have been higher
Techniques
Keep in mind that many incidents/breaches fall into multiple categories.
Around half involved "hacking"
1/3 included social engineering
Around 1/3 involved malware
They say only around 4% involved a physical component, which I find fascinating. Coming from such a major report, this could lead some to spend less on physical pentesting. Although, maybe that 4% were the ones that mattered most.
Victims
Almost half the victims were small businesses
Attack types vs. industries
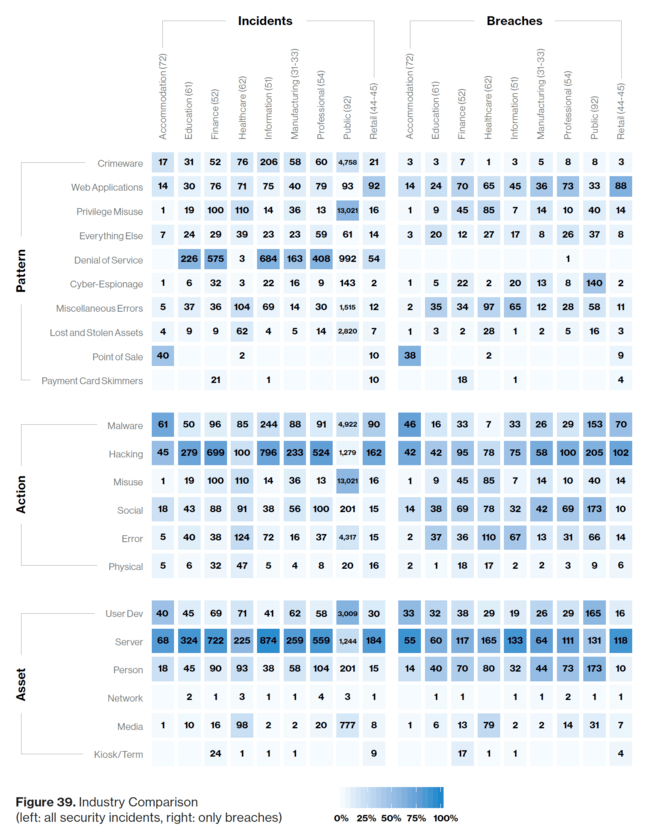
Denial of service and hacking was popular across many industries
The server itself was the most popular target
Hospitality (Accommodation) had series issues with malware and hacking
Their key analysis points
Executives are being targeted (between and 9 and 12 times more than in the past)
Attackers are following companies into the cloud
Web-app-based payment systems are catching up to physical terminal compromises. This is interesting, since I would have thought this crossover would have happened a long time ago. They say Chip and Pin could be a major factor in this
Ransomware is still a very common technique
Maybe we need to build campaigns that more specifically target mobile?
Phishing is quite effective on mobile devices
Miscellaneous Errors continue to represent in many patterns, especially where the industry is usually understaffed and underskilled (healthcare, education, etc.)
Espionage is the biggest issue in the public sector
Other observations
Thanks to Anton Chuvakin > for seeing these.
Over half of the breaches took multiple months to discover
Only around 6% of breaches were the result of exploiting vulnerabilities (why hack when you can just log in?)
Malware was delivered by email in 94% of cases (oldie but goodie)
Anton makes the great point that data at rest isn’t the only target anymore; if they can compromise what customers type data into, they get the same data (albeit less)
My takeaways
If you stay up on security news there weren’t too many surprises, but the data backing continues to be exemplary
Protect your VIPs (including executives)
With 1/3 of attacks involving internal actors, and 15% involving misuse by authorized users, they make a pretty strong push for monitoring insiders (also known as employees)
Errors were involved in 21% of attacks, which is still extremely high. Do your best to avoid own-goals
Overall, another solid release. Well done to the team.
And it really is worth taking the time to at least skim the full report >.