The Hierarchy of Information Security Talks
Dave Aitel commented back in September > that he thought "junk hacking", i.e., testing blenders and bed-warmers for security vulnerabilities, was a huge waste of time.
He writes:
So in any case, enough with the Junk Hacking, and enough with being amazed when people hack their junk.
I agree with him that this type of IoT-focused talk can be empty, but I think he missed a critical point:
Most talks at most security conferences are exactly the same. It’s a problem that applies to our industry’s conferences in general, not just to IoT-related content.
When you stare into the eyes of the common security talk, it’s usually about some slightly different way to hack a widget. Maybe that widget is a web or mobile application instead of a blender, but isn’t that a distinction without a difference?
Dave wrote:
Yes, we get it. Cars, boats, buses, and those singing fish plaques are all hackable and have no security.
Fair enough. But I’d argue we could say the same for 95% of security talks.
Let’s try frameworks:
Yes, we get it. Web and mobile frameworks are all hackable and have weak security.
Or hardware:
Yes, we get it. Firmware is hackable and has weak security.
If we applied that attitude across our industry we’d have one conference a year.
To me it comes down to one question:
Do we really think that, as an industry, our biggest problem is not having enough vulnerabilities?
That seems to be the problem that most conferences are solving. Finding more vulns. And in a world where most breaches are from issues more than a year old, that just doesn’t seem like a defensible position anymore.
That’s not to say that all talks are the same, though. Some talks are about new tools for performing existing attacks, and there are a few that are about new tools for doing new attacks, which are quite rare and can definitely be valuable.
But the best talks—at least in my opinion—are those that introduce new ways to fix information security problems, not just to identify or exploit them. An example would be Dan Geer’s keynote at Blackhat 2014.
When compared to that standard, most of today’s talks become noise in the background. Is there really that much difference between new research showing how to hack a popular web framework and showing dangerous open ports on a refrigerator?
They’re definitely different, but I think the line is more blurry than we’d like to believe.
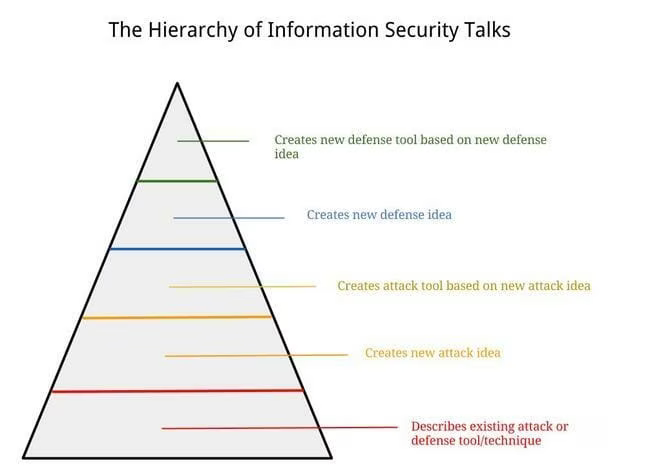
So to gain some perspective I’ve tried to put together a hierarchy of ambition when it comes to infosec talks. They go from top to bottom in terms of the ability to make a difference in the industry vs. simply explaining or iterating.
Here are the tiers:
Creates a new defense tool based on a new defense idea
Creates new defense idea
Creates a new attack tool based on a new attack idea
Creates a new attack idea
Describes an existing attack or defense tool or idea
The levels aren’t perfect, but hopefully the model accomplishes the primary goal of putting creation above repetition, and fixing above breaking.
Comments on how stupid I am are welcome and appreciated.
Notes
I believe there is plenty of "old" wisdom out there that people have forgotten and could benefit from in the form of concise and powerful summarization, so just because something lives at the bottom level doesn’t mean it lacks value.
Many of the talks I’ve given are at the lower levels of this hierarchy, so this is a reminder for me as much as anyone else.
There is no question that attack research is valuable for our industry. It’s often the pursuit of attacks that lead to ideas about defense. My main point was that unless we keep that goal of *fixing* things in mind the attack conversation becomes a diversion rather than a means.
I could imagine another spectrum that covers technical eliteness, e.g., going from little to no technical detail, to describes technology used, to basic technical depth, to deep technical depth. It could be a two-dimensional grid, with the ambition on the y and the technical depth on the x.