Getting Visual XML Output from nmap
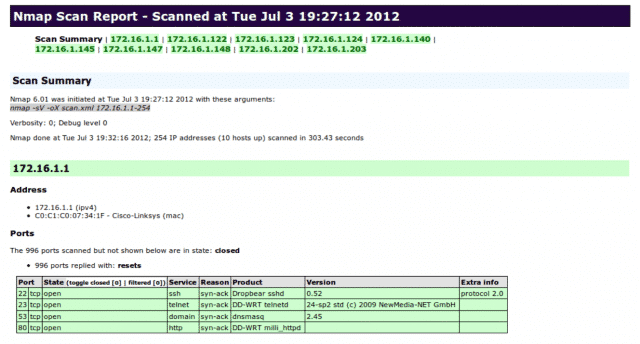
We all love nmap. Despite the entry and rise of many other scanners, nmap is always my first choice.
Most people just use its default output option, which is to the console.
But my favorite (and default) output option is all three, using -oA.
# Double-verbose, increased speed, output to standard/greppable/XML
nmap -vv -T4 -oA SESSIONNAME TARGET
The XML output, which you can also give on its own as -oX, allows you to read the results in a webpage with some slick formatting like that seen in the first image above.
What it does is uses an XSLT file to add styling to the XML. By default that XSLT points to a specific, local file on the host you’re running nmap from. This can be problematic and annoying, with multiple possible paths existing based on how you installed nmap.
But there’s good news. If you add --webxml to your command string it’ll produce an XML that has the web version of the XSLT so it doesn’t matter how or where nmap was installed!
# Double-verbose, increased speed, output to standard/greppable/XML, web XSLT
nmap -vv -T4 –webxml -oA SESSIONNAME TARGET
Consider adding -oA and --webxml to your default nmap command line.