Entering Promiscuous Mode on OS X
December 29, 2014
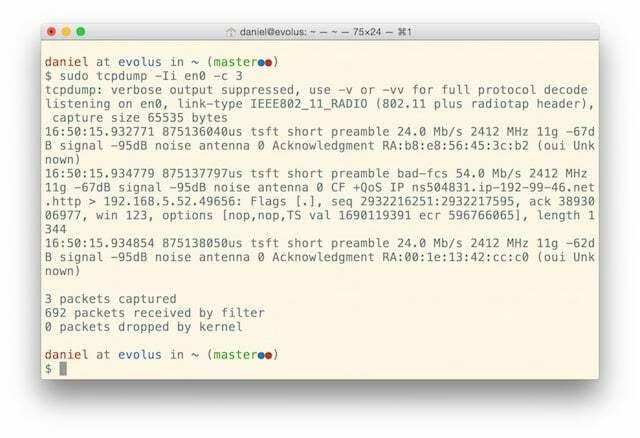
As a security professional on OS X, we often need (or simply want) to see all packets hitting our wireless interface rather than those just destined for it. As it turns out it’s remarkably easy to do with OS X.
Simply add the -I option to your tcpdump command (also works with tshark). From tcpdump’s manual:
Put the interface in "monitor mode"; this is supported only on IEEE 802.11 Wi-Fi interfaces, and supported only on some operating systems.
tcpdump -Ii en0
The cool thing about this is that it will show not just packet data, but also radio data, as shown in the capture above.
Enjoy.
[ NOTE: My book on tcpdump will be released sometime in 2015. ]