The DROWN SSL Attack
Source: DROWN Attack >
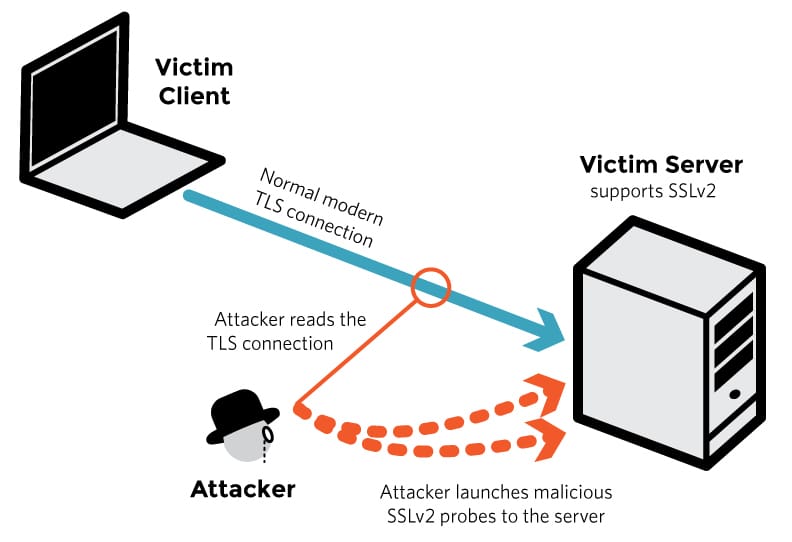
There’s a new attack against SSL, specifically SSLv2.
Similar to other named attacks, DROWN uses multiple SSLv2 connections to extract key data.
SSLv2 is supposed to be deprecated, but far too many sites still have it fully supported. Others that have supposedly upgraded to TLS, but still allow fallback to SSLv2 if the client asks for it.
Summary
DROWN utilizes SSLv2 to extract key data, which can lead to the ability to decrypt encrypted sessions
The fix is to ensure that you’re not only supporting TLS, but that you’re specifically disallowing SSLv2, even when the client asks for it
For the fix you should make sure you’re configured correctly as well as upgrade your HTTPS encryption package (such as OpenSSL) as soon as possible
Notes
There’s also another way to be compromised, i.e. if you use that same RSA-based key somewhere else that’s compromised, and the key is used to extract data from your HTTPS stream even though you don’t have the vulnerability there.
Technical paper: https://www.drownattack.com/drown-attack-paper.pdf
More information: https://www.drownattack.com