Analysis of the 2018 F5 Threat Intel Report

F5 just released a threat intel report > that covered 433 breach cases spanning 12 years, 37 industries, and 27 countries.
When companies release reports like these I go through them and extract nuggets for those who don’t have time to look at the full report. You will find the extraction for this report below.
Applications were the initial target in 53% of the breaches.
Identities were the initial target of 33% of them.
The apps are evidently the target, but you have to be cautious about this message because F5 is selling WAFs. So much of this kind of research is done in DIRECT coordination with the marketing and product teams, so I am always weary when someone discovers a trend that happens to help their exact product.
86% of the U.S. population has had their SSN compromised. Interesting stat.
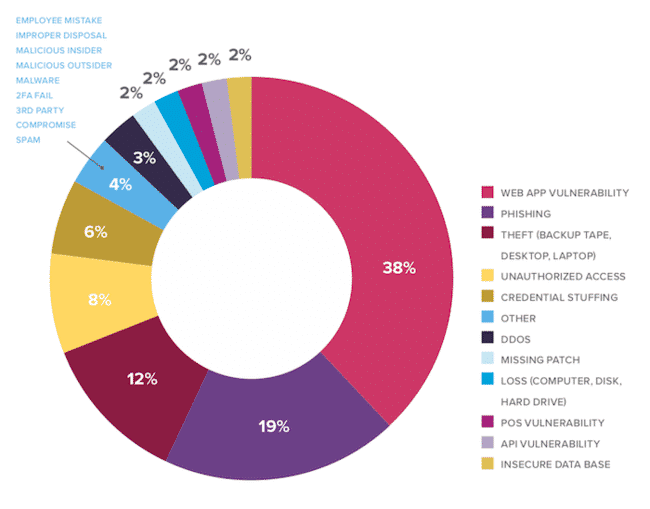
Root cause analysis
38% breaches by web app vulnerability, 19% by phishing, 12% stolen assets, 8% unauthorized access (not sure what that means exactly), and 6% credential stuffing. When I read lists like this I think about what fundamentals would solve these issues. For web app vulns it’s an appsec program, clearly, phishing is hard because you need a multi-layered defense and the attacks are constantly evolving, and the stolen assets piece is mostly just good asset management and organizational discipline.
They break down the web vulnerabilities in a strange way. They don’t use OWASP or any other main classification, but rather mix the software type (forums) with vendors, e.g., vBulletin. Using that system they come up with forum software being #1, with SQL injection being second. This is strange because one is a target and the other is a vulnerability. In other words, if you have broken forum software, that means it’s vulnerable to XSS, or SQL Injection, or some other thing. So I think they’re mixing apples with hatchets here. Not super useful.
Also wondering where XSS, CSRF, XSRF and other web vulns are in the list.
The industries that were attacked the most were Healthcare, Technology, Online Gaming, Financial, Online Forums, Government, and Social Networks (the list continues).
But in terms of impact, those hit hardest were Retail, Government, Technology, Financial, and Online Gaming. The thing I see in common here is a strong requirement for availability.
Then if you look at the number of records breached, it’s a different order again: Technology, Cybercrime, Social Network, Adult, Retail, Financial, Online Forum, Government, and the list continues.
Out of the 433 cases, 42 of the companies had no idea they were breached for years.
Credentials are rising in popularity as targets relative to credit cards because credentials are often used elsewhere and therefore add additional value, whereas there’s so much credit card data out there that the prices are lower.
Most companies are still using weak hashing mechanisms to protect passwords.
Lots of fake people are being made and used to do various things.
Third party breaches are hurting companies as well.
Great work to the F5 team on this research! If you liked the summary, consider going over to read the entire report >.