The Government Solution to AI Inequality Might Be UBI + Really Good Games
AI's barbell economy will need both UBI and immersive entertainment
This is some of my favorite, most popular, and latest content. You can also browse and search the archives.
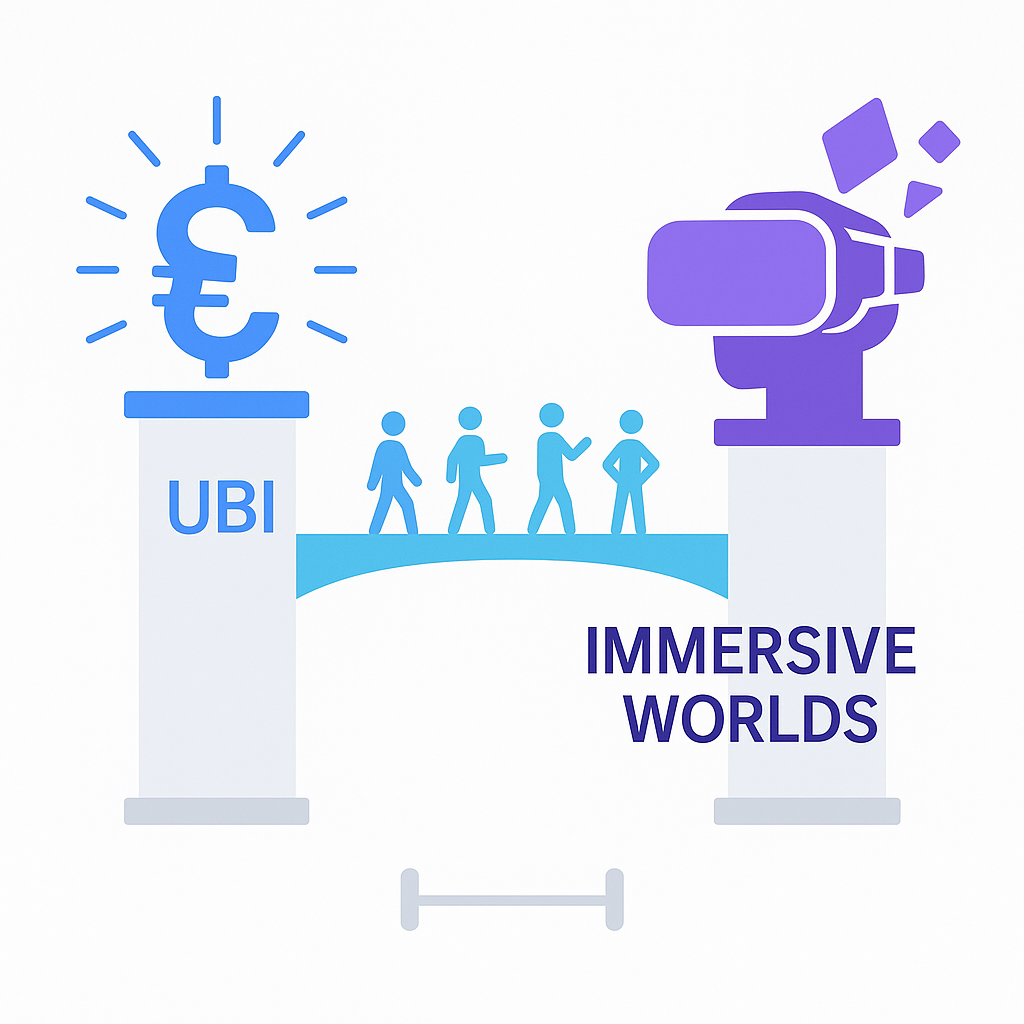
AI's barbell economy will need both UBI and immersive entertainment
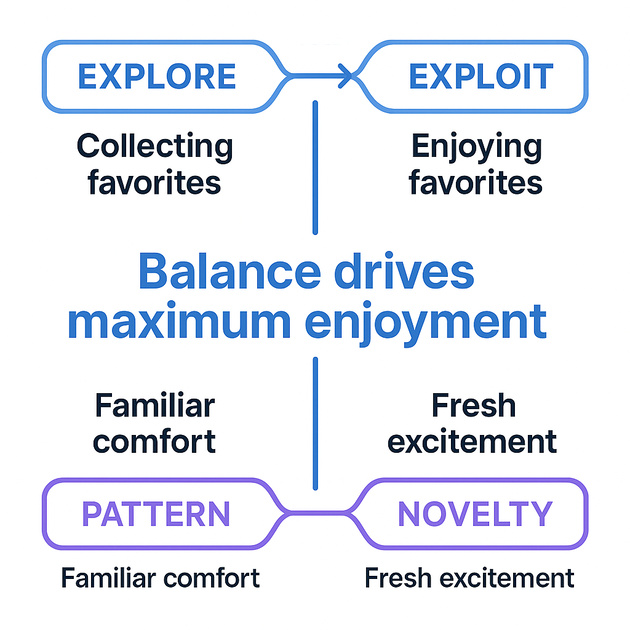
Understanding how oscillating between exploration and exploitation unlocks maximum enjoyment from life

Why a major crash, AGI, and millions of jobs replaced aren't mutually exclusive
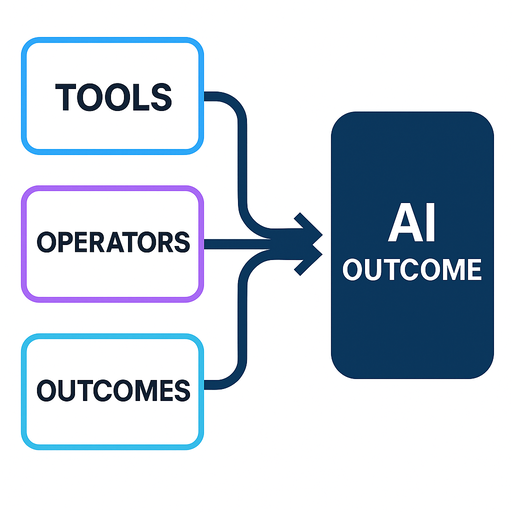
The collapsing of the traditional three-part model explains why AI is so economically disruptive

What if our world models are just as emergent and flimsy as AI's?

We lost our common frames, and the ability to tell the difference between disagreement and hate

An extremely clear vision of how AI will completely disrupt everything within 1,000 days
A list of different ways we limit ourselves creatively